Solution
A solution for every information security challenge, no matter your role or industry.
.png)
.png?width=179&height=525&name=Vector%20(14).png)
.png?width=198&height=442&name=Vector%20(15).png)
What solution are you looking for?
Security, elevated.
SureCloud’s Aurora platform helps organizations effectively manage information security risks and gain complete visibility of their operations. The highly innovative platform provides powerful insights to help your organization stay ahead of threat actors and constantly evolving compliance standards. With Aurora’s out-of-the-box automation capabilities, you can transform your efficiency and dramatically reduce your operating costs.
-
Powerful visualization capabilities
Total visibility of your risk and compliance management performance to help you manage, monitor and optimise your programs. -
Single pane of reporting glass
Whether you’re the technician or the CEO, see your key information security risks at a glance.
-
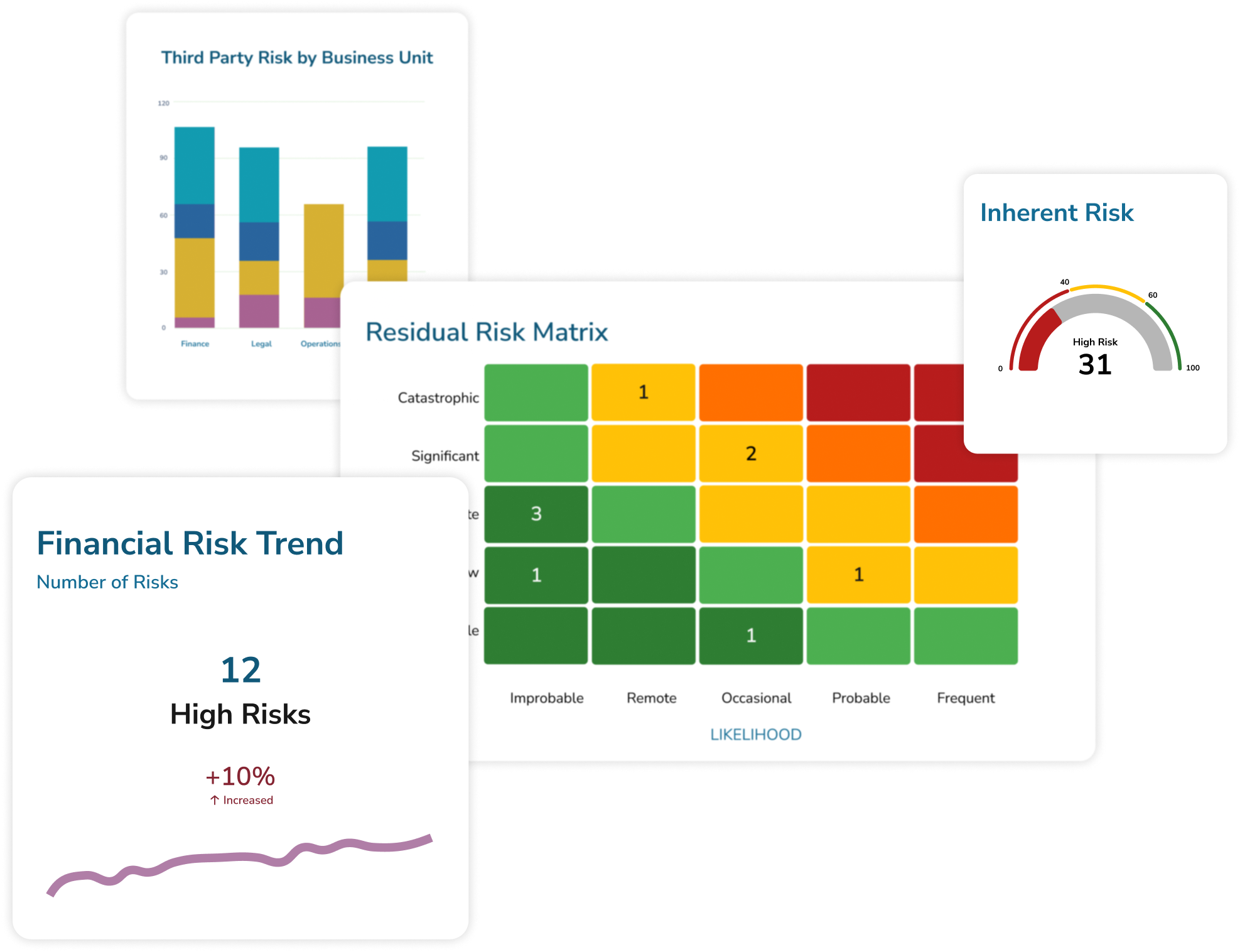
Real-time risk analytics
Demonstrate the ROI of your risk and compliance operations, and impart meaningful knowledge to stakeholders. -
Define and quantify risk
We offer varied risk assessment approaches such as IT Risk ISO 27005, Enterprise Risk ISO 31000 and cyber risk quantification (CRO).
-
Fully embedded continuous control monitoring (CCM) functionality
Dramatically reduce the time spent testing your control configuration, preparing for certifications and auditing compliance.
-
Peer performance metrics
Transform data into insights and benchmark performances against your peers.
-
Highly flexible, yet robust workflows
Empower your team to reconfigure custom dashboards and reports with the help of an easy-to-use workflow builder.
-
No-code workflow and report builder
Aurora’s no-code architecture and intuitive GUI means you can easily undertake complex configuration tasks, no matter your level of technical ability.
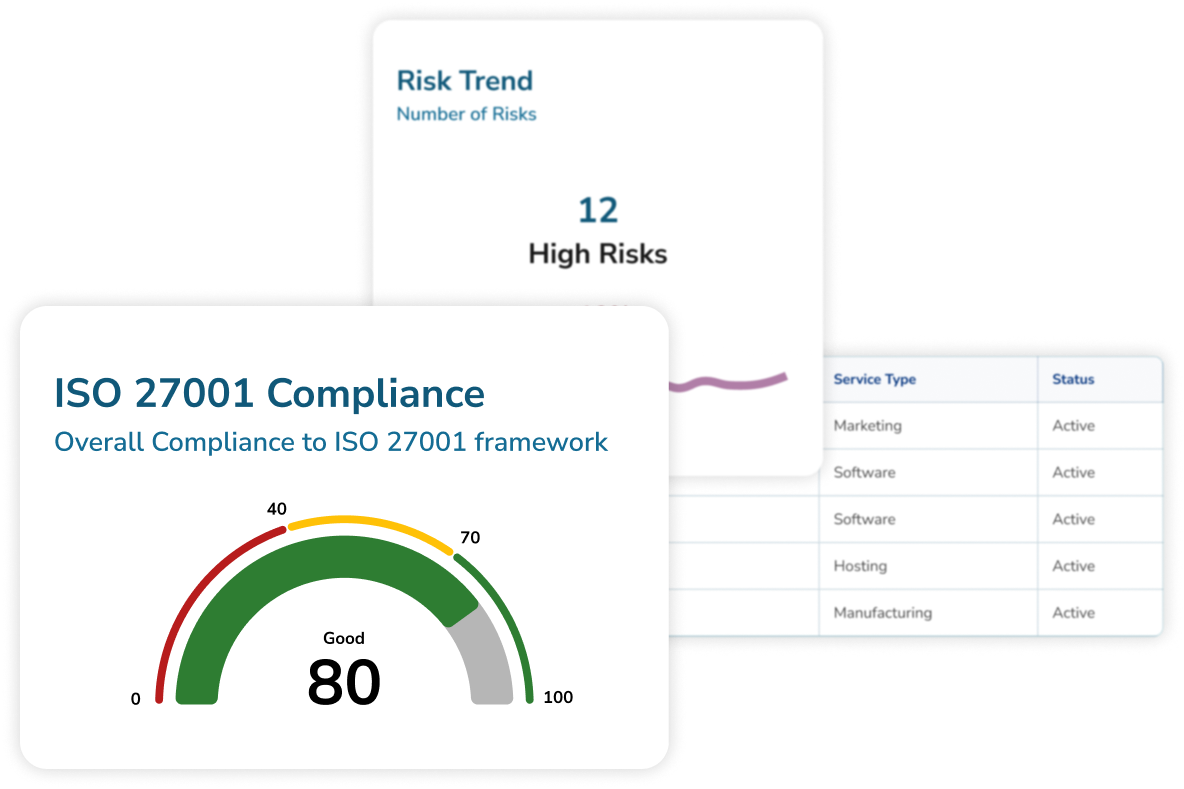
Powerful visualization capabilities
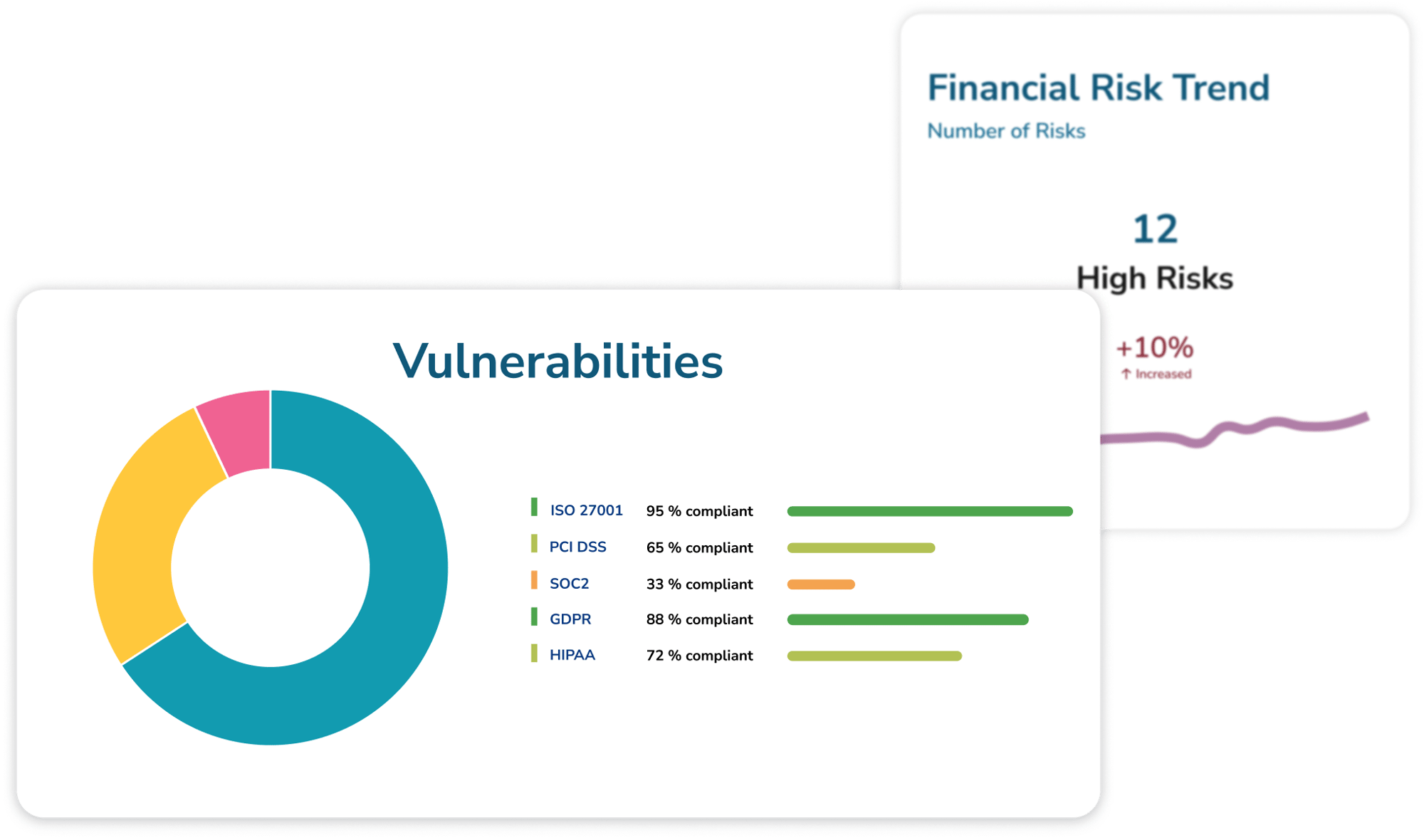
Single pane of reporting glass
Whether you’re the technician or the CEO, see your key information security risks at a glance.
Real-time risk analytics

Define and quantify risk
We offer varied risk assessment approaches such as IT Risk ISO 27005, Enterprise Risk ISO 31000 and cyber risk quantification (CRO).

Fully embedded continuous control monitoring (CCM) functionality
Dramatically reduce the time spent testing your control configuration, preparing for certifications and auditing compliance.
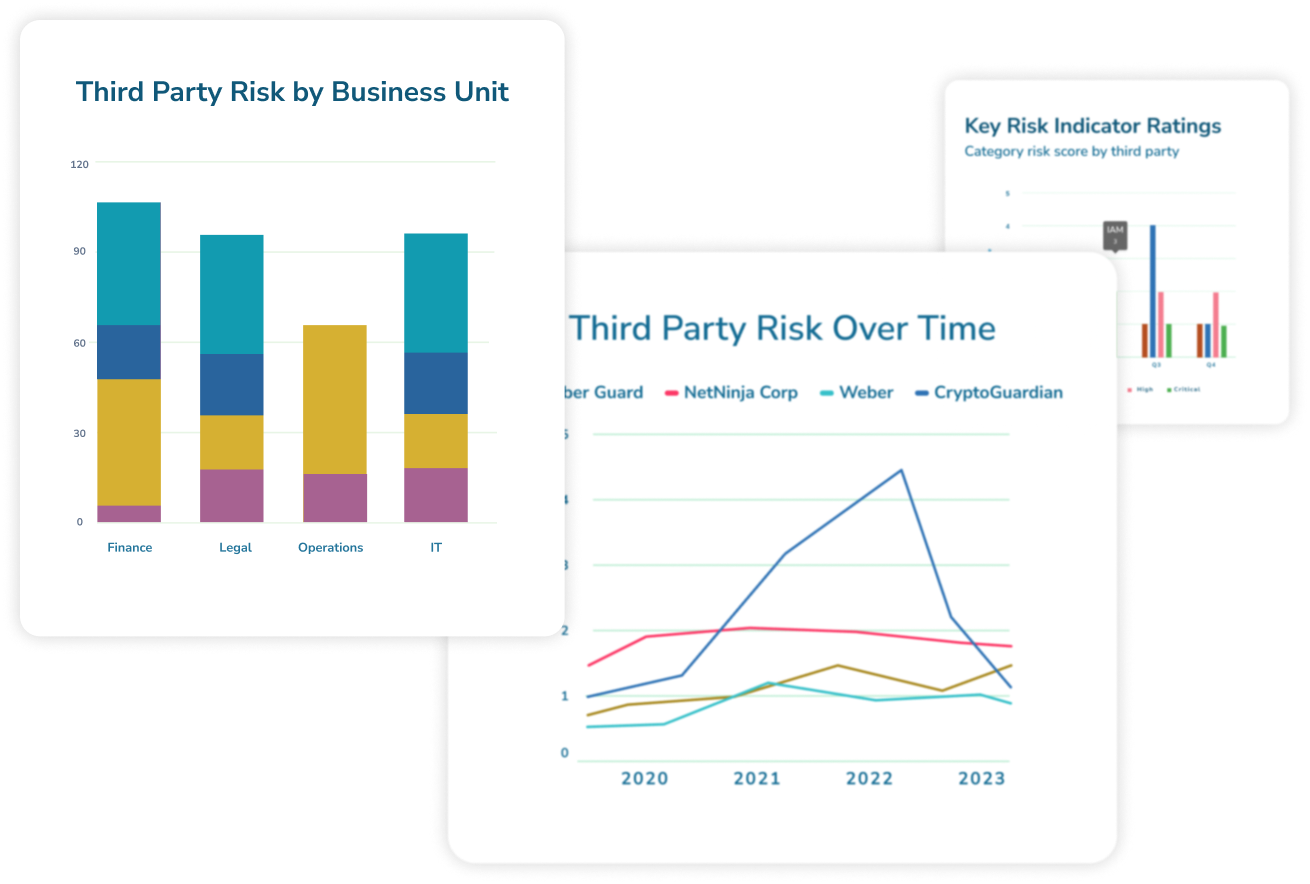
Peer performance metrics
Transform data into insights and benchmark performances against your peers.
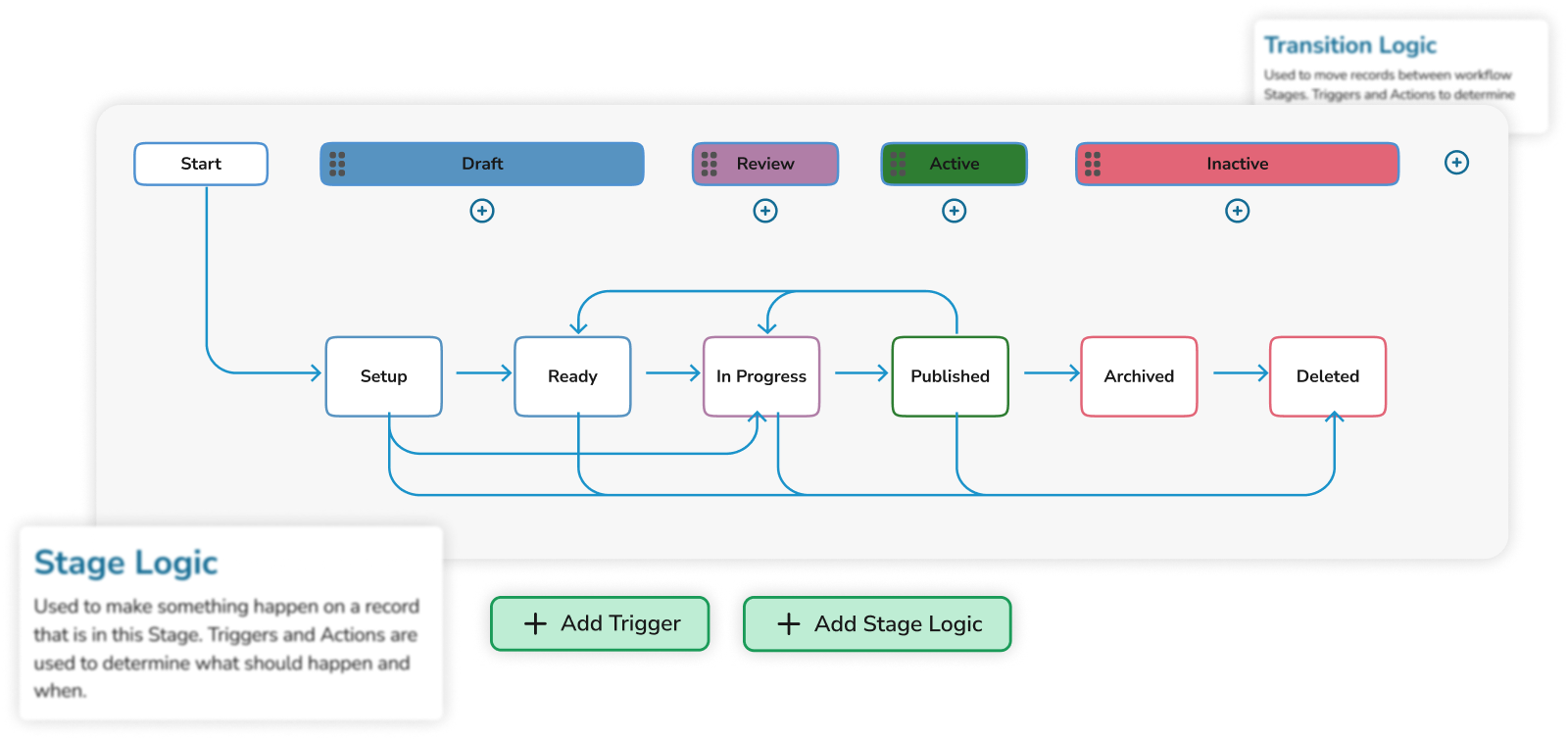
Highly flexible, yet robust workflows
Empower your team to reconfigure custom dashboards and reports with the help of an easy-to-use workflow builder.
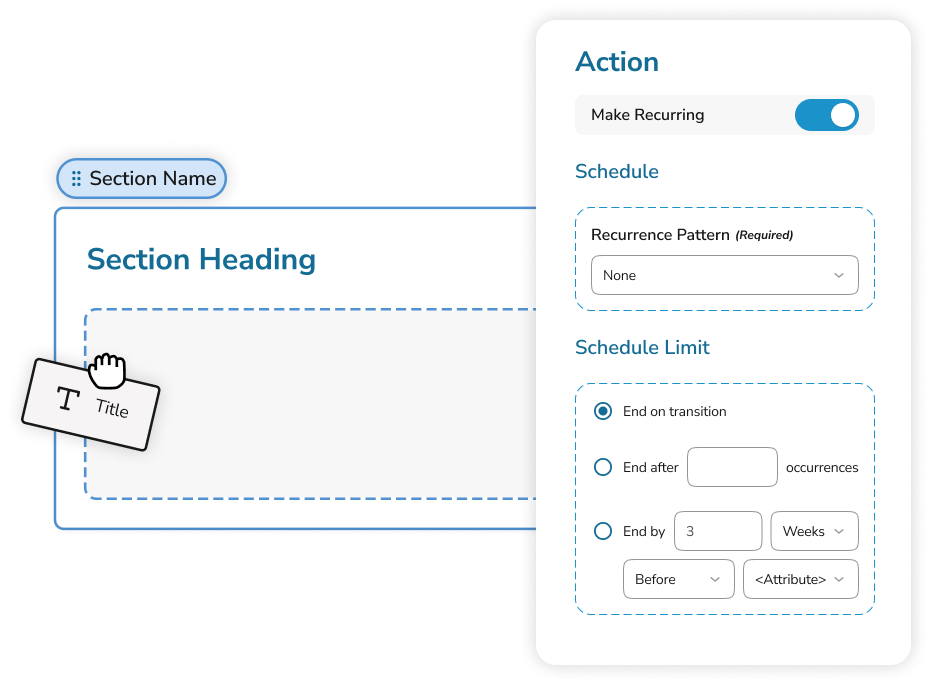
No-code workflow and report builder
Aurora’s no-code architecture and intuitive GUI means you can easily undertake complex configuration tasks, no matter your level of technical ability.
Integrated GRC
If you’re currently held back by poor insights into program performance and can’t adapt your GRC software to your organization’s unique needs, Aurora is designed to help you remove these barriers with the ability to calculate ROI metrics and drag-and-drop configuration.
With intelligent, real-time data dashboards and unique adaptability, Aurora helps you transform
uncertainty into knowledge.

Third-Party Risk Management
Proactively manage key risks throughout your vendor landscape

Data Privacy Management
Govern and track your GDPR, CCPA and other legal requirements

Compliance Management
Manage, continuously test and report on your compliance status

Risk Management
Centrally assess, prioritize and manage your key technology risks

Internal Audit Management
Centralize & manage your processes and program

Business Continuity
Continuously manage and assess your organization’s ability to remain operational

Policy Management
Ensure your business users attest to all information security policies

Incident Management
Record, investigate and remediate all breaches

Vulnerability Management
Prioritize, track and report on key vulnerabilities within your organization
.png?width=106&height=498&name=Vector%20(16).png)
What’s your role?
How can SureCloud help make your job that little bit easier?
Find out how our solutions can help you succeed.
CISO
Chief Information Security Officer
As a CISO, you’ve got a major responsibility on your shoulders. You’re the trusted person working to make sure the organization’s security measures align with business objectives and regulatory requirements.
Feeling the pressure?
What if you had a central platform that could help you:
-
Balance security with business objectives?
-
Provide a business lens on security?
-
Reduce the risk and impact of breaches?
-
Balance security with regulatory and legal requirements?
Then you might want to hear more about Aurora.
CRO
Chief Risk Officer
Are you the person responsible for identifying, analyzing and mitigating risks in your organisation? As a CRO, you play a vital role in continually reviewing factors that could harm investments or business units – so it’s vital you can communicate risks in a way that leaders understand.
Take control of risk.
Ask yourself the following questions:
-
Do you need a simpler way to connect the dots between technical and business risks?
-
Would you like to better communicate risk insights with stakeholders?
-
What if you could calculate the impact of potential risks to help you make better decisions?
With Aurora, you can.
