- 3rd Nov 2025
- 1 min read
The 5 Pillars of DORA Explained – Building Digital Resilience in Financial Services

- Written by
In Short..
- Run DORA as a loop: Identify, protect, test, report, and improve—treating resilience as an ongoing operating model, not a one-off project.
- Keep one source of truth: Maintain a single live register for services, systems, data, and ICT providers to anchor every control and audit.
- Automate and align: Map controls once across DORA, ISO 27001, and NIS2, and automate evidence collection to prove they run in practice.
- Build resilience by design: Integrate incident reporting, testing, and supplier oversight into daily operations so compliance becomes continuous.
By mastering these pillars, financial institutions can turn DORA from a compliance exercise into a lasting framework for operational resilience.
Introduction
DORA (the Digital Operational Resilience Act) is now in force across the EU. From January 17, 2025, financial entities have moved from awareness to action. Supervisors are aligning how major incidents are reported, how resilience testing runs, and how critical ICT providers are overseen. If you work in EU financial services—or support it as an ICT provider—this is the time to turn plans into proof.
In our Complete Guide to DORA, we explained who DORA affects. Here, we’ll unpack how it works in practice—through its five foundational pillars—so you can assign owners, put the right controls in place, and keep audit-ready evidence without overbuilding.
For the full source text, see Regulation (EU) 2022/2554 on EUR-Lex.
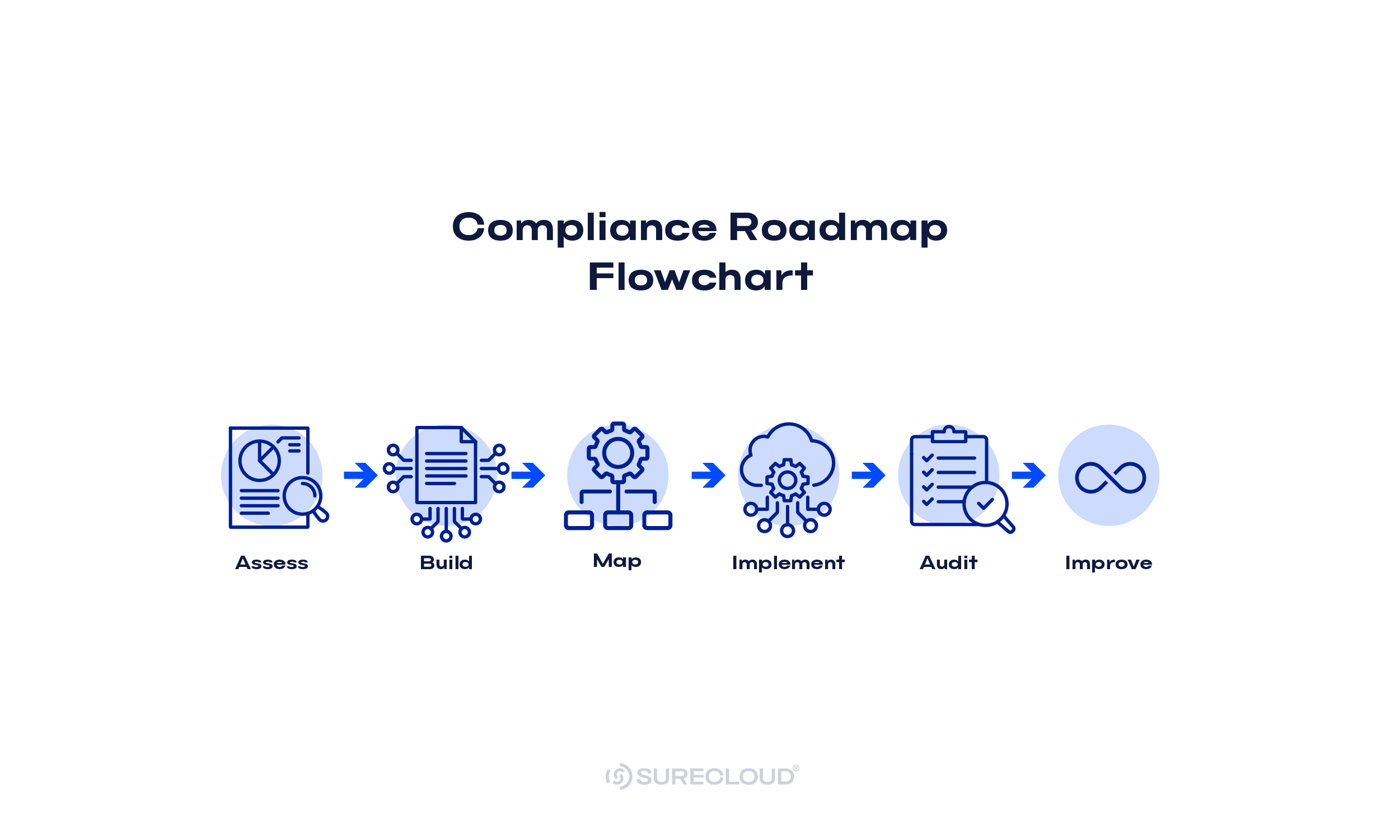
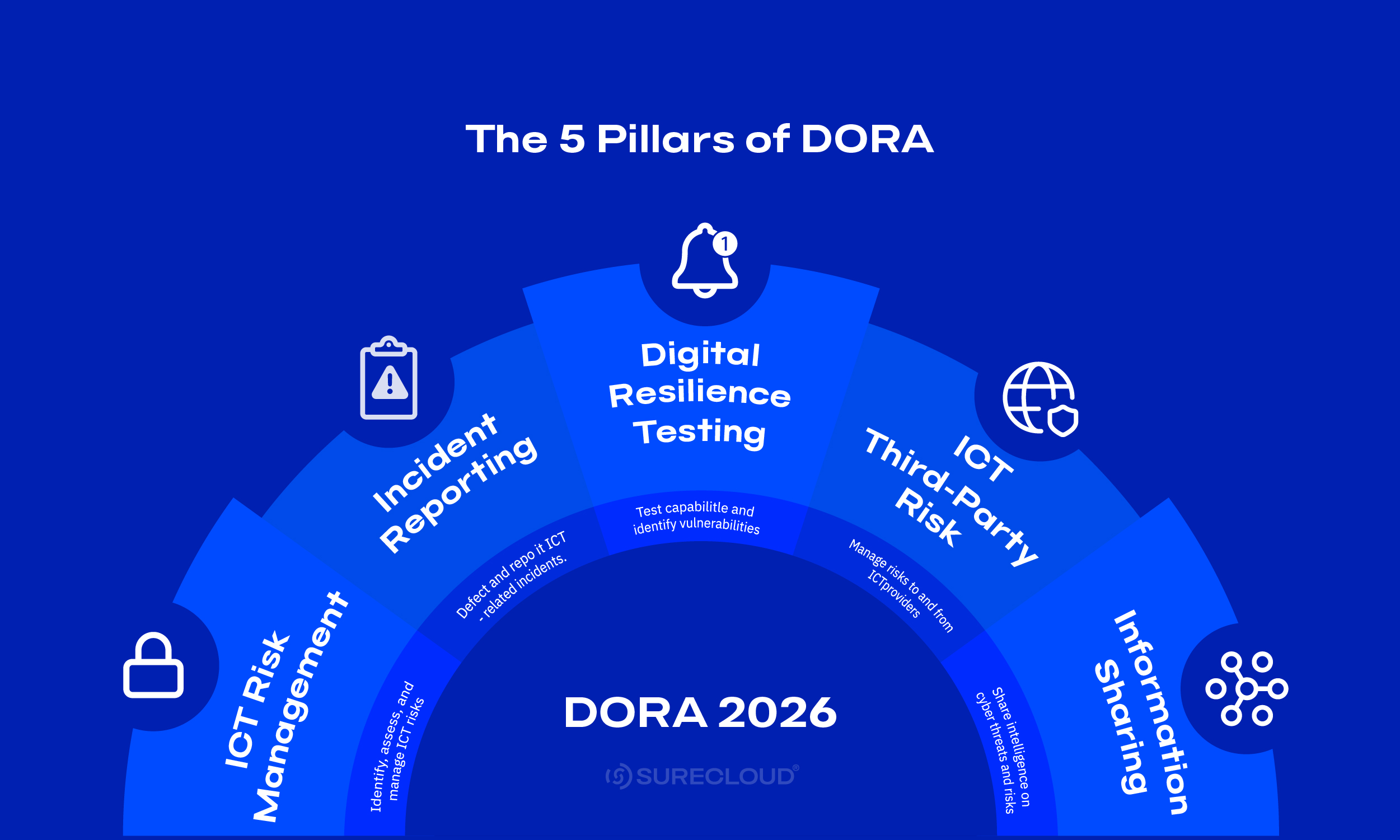
What Are the Five Pillars of DORA?
DORA organizes its duties into five working parts you can run as a program:
-
ICT Risk Management
-
Incident Reporting
-
Digital Operational Resilience Testing
-
Third-Party Risk Management
-
Information Sharing
These DORA pillars give teams a simple structure for day-to-day compliance and a shared language with auditors and supervisors.

Pillar 1: ICT Risk Management Framework
What DORA Expects
Run a documented, end-to-end ICT risk program that covers the full cycle:- Governance: an executive owner, clear decision rights, named control owners, and board reporting
- Identification: a live register of business services, supporting systems, data, and ICT third parties (with criticality and dependencies)
- Protection: preventive controls across identity and access management (IAM), configuration/change, hardening, backups, and secure development
- Detection: monitoring for key events and control health; thresholds for “major” vs. routine issues; reliable logging and retention
- Response & recovery: tested playbooks, RTO/RPO targets, contact lists, and post-incident reviews with tracked fixes
This is the engine of the DORA framework. Supervisors expect proof of operation, not policy alone, so design for evidence from day one.
The Operational Checklist
- One register: keep services, systems, data, and ICT suppliers in a single view with owners, criticality, and dependencies
- Lean control library: start with access, configuration/change, backup/restore, logging/monitoring, vulnerability, and secure development
- Map once: tag each control to DORA requirements and to ISO/IEC 27001 Annex A so you can test once and reuse evidence
- Cadence: define method, frequency, pass/fail, and retest after fixes
- Evidence first: store approvals, tickets, logs, configuration exports, restore results, and review notes where auditors can find them
- Close the loop: feed incident and testing findings back into risk; update owners and controls; track time-to-close and retest pass rates
In Practice: A compact control set mapped to DORA + ISO 27001
|
Control |
DORA outcome |
ISO/IEC 27001 theme |
Owner |
Method & cadence |
Evidence |
|
Access management |
Governance, Protection |
Access control; Identity & authentication |
Identity Lead |
Quarterly privileged-access reviews; weekly anomaly checks |
Review sign-offs, access change logs, SIEM alerts/closures |
|
Backup & recovery |
Recovery, Protection |
Backup/restore; Continuity |
Infrastructure Lead |
Monthly restore tests; quarterly failover drills (meet RTO/RPO) |
Backup job logs, restore results, drill reports, change tickets |
|
Logging & monitoring |
Detection, Governance |
Logging; Monitoring |
SOC Manager |
Daily SIEM health; monthly rule tuning; documented “major incident” thresholds |
SIEM dashboard, rule-change records, incident timelines |
Why This Matters
When governance, identification, protection, detection, and recovery run as one cycle, you reduce incident impact, shorten audits, and create repeatable DORA ICT risk management with audit-ready proof.
Pillar 2: Incident Reporting
The Reporting Clocks
DORA harmonizes major ICT incident reporting with EU-wide timelines and templates:
- Initial notification: within 4 hours of classifying as major and no later than 24 hours from detection
- Intermediate report: within 72 hours
- Final report: within 1 month
Use the ESAs major-incident reporting RTS/ITS templates as the field model so your forms and workflow align cleanly from detection to authority.
Harmonized Thresholds (What Counts as “Major”)
The ESAs define classification criteria and materiality thresholds (service impact, customers affected, data affected, and time to recover). Your internal thresholds, forms, and dashboards should align to the ESAs field names. That way, analysts don’t re-key under pressure, and leadership sees the same numbers that go to the authority.
What’s New For 2026
Unified templates and procedures from the ESAs reduce national variation. As national tooling matures through 2026, expect more consistent content and timing, and fewer one-off forms.
Runbook Basics
- Pre-build the 4h/24h/72h/1-month data fields
- Rehearse quarterly with a timed tabletop; capture how long evidence takes to assemble
- Maintain a living incident evidence pack: timeline, root cause, business impact, containment/recovery actions, and lessons learned
- After the final report, close corrective actions and retest controls tied to the root cause
Why This Matters
Getting the clocks and fields right cuts rework in the first 24 hours, keeps leadership and regulators on the same facts, and reduces the risk of late corrections. Aligning to the ESAs template names and keeping a ready evidence pack also shortens audit cycles and avoids divergence as national tooling converges in 2026.
Pillar 3: Digital Operational Resilience Testing
What DORA Expects
DORA defines two types of operational resilience testing:
- Baseline testing: vulnerability scans, configuration reviews, restore/failover drills, and tabletop exercises on a defined cadence
- Threat-Led Penetration Testing (TLPT): required for entities designated by their competent authority. TLPT aligns to TIBER-EU, with scope and frequency set by that authority
Frequency At A Glance
|
Entity type |
Testing expectation |
|
Designated for TLPT |
TLPT at least every 3 years (frequency may be adjusted by your TLPT authority), plus year-round baseline testing |
|
Not designated |
Risk-based baseline testing with clear evidence and remediation tracking |
Note: exact TLPT scope and cadence are set by your TLPT authority; align your plan and supplier participation early.
Operating Approach
- Maintain a rolling plan tied to critical business services and risks
- Link each test to the specific control(s) it proves; record results, owners, deadlines, and retests
- For TLPT, focus on critical functions and realistic threat scenarios; pre-agree legal/safety guardrails and involve key suppliers
Why This Matters
Planned, repeatable testing turns assumptions into evidence. It shows controls work in practice, focuses fixes where risk is highest, and prepares you for TLPT without last-minute scrambling.
Pillar 4: Third-Party Risk Management
What DORA Expects
DORA introduces EU-level oversight for critical ICT third-party providers (CTPPs)—cloud, SaaS, and infrastructure platforms many firms rely on. A designated Lead Overseer (one of the ESAs) coordinates examinations with Joint Examination Teams (JETs). Your firm stays accountable for outcomes even when services are outsourced.
Contracts, Evidence, and the Shared Boundary
- Flow-down obligations: embed terms for incident cooperation (timelines that support regulatory reporting), participation in testing where relevant (including TLPT support), resilience outcomes (RTO/RPO targets), reporting/audit rights, data-location controls, change notifications, and exit/substitution rights
- Evidence on a cadence: request supplier artifacts on a schedule (pen-test summaries, recovery drill results, certifications, uptime/incidents, sub-processor lists) and track expiries
- Concentration oversight: monitor exposure by provider, region, and service; set mitigations for “too-big-to-fail” scenarios
- Shared accountability boundary: you carry the regulatory duty; suppliers must cooperate and evidence their part so you can meet it
Why This Matters
Most resilience gaps hide in the supply chain. Clear flow-down terms, recurring evidence, and visibility of concentration risk turn third-party reliance into managed, provable DORA compliance.
Pillar 5: Information-Sharing Arrangements
Purpose
DORA encourages cyber-threat information sharing so firms can spot attacks earlier and respond faster. The goal is collective resilience: one entity’s signal becomes everyone’s head start.
Guardrails
Sharing should happen in trusted communities and follow confidentiality, data-protection, and competition-law rules. Keep legal and privacy teams involved. Define what can be shared (e.g., indicators of compromise, TTPs, hardening guidance) and what must be withheld or anonymized.
How it Looks in Practice
Join a sector body like FS-ISAC or a national financial-sector sharing group. Set owners for ingest → assess → act:
- Ingest: pull daily threat feeds and alerts
- Assess: validate relevance against your estate and suppliers
- Act: update detections, block indicators, and harden configurations; record what changed and why
Keep a short log of items received and actions taken—this shows value and supports audits.
Why This Matters
Turning shared intelligence into detections and hardening actions cuts time-to-detect and keeps firms on the same facts during sector-wide campaigns. Anchoring participation to Article 45 and documenting the steps makes the practice safe, repeatable, and audit-ready.
Bringing It Together: The DORA Compliance Ecosystem
The closed-loop
The five pillars operate as a loop you run every day:
- Identify services, systems, data, and suppliers (Pillar 1).
- Protect with mapped controls and ownership (Pillar 1).
- Test those controls on a cadence; run TLPT where required (Pillar 3).
- Report major incidents on time with consistent fields (Pillar 2).
- Improve by closing actions, updating risks, and applying shared intelligence (Pillars 1 & 5), including supplier follow-through (Pillar 4).
Pillars 4 and 5 (third-party oversight and threat intelligence) overlay the entire loop, shaping control priorities, tests, and incident handling end-to-end.
Link to ISO 27001 and NIS2
ISO/IEC 27001: many controls overlap (access, logging, backup, change, vulnerability). Keep one control library and tag each control to DORA and Annex A so you test once and reuse evidence across frameworks.
NIS2: incident timing and escalation are similar in spirit. Align data fields and playbooks so teams don’t duplicate effort when one event touches both regimes.
Practical rule: if a control or process already exists, map it; only create new ones where DORA adds a clear requirement (e.g., major-incident thresholds, supplier registers, TLPT governance).
How SureCloud Helps Operationalize the Five Pillars
SureCloud gives you one place to run the DORA framework day to day. Keep a single register, map controls once, automate evidence, and report with confidence.
|
DORA Pillar |
How SureCloud Helps Operationalise It |
|
Pillar 1: ICT Risk Management |
Use Risk Management and Compliance Management to maintain one register of services, systems, data, and suppliers, and to own a mapped control library with clear owners and cadence. Continuous Control Monitoring verifies critical controls between audits, while Automated Evidence Collection schedules and versions proofs (e.g. Microsoft 365, Google Drive, Box, Dropbox) so you can demonstrate operation—not just intent. |
|
Pillar 2: Incident Reporting |
Incident Management standardises intake to closure with fields aligned to the ESAs RTS/ITS templates and timers for the 4h / 24h / 72h / 1-month cadence. Ownership, SLA clocks, and status are visible at a glance, while Automated Evidence Collection links logs, approvals, and attachments to each case for fast, consistent submissions. |
|
Pillar 3: Digital Operational Resilience Testing |
Plan baseline testing and TLPT tasks in Compliance Management—assign owners, due dates, and retests—while Continuous Control Monitoring checks key controls between exercises to catch drift early. Store reports and sign-offs with Automated Evidence Collection so your DORA testing pack is always audit-ready. |
|
Pillar 4: Third-Party Risk Management |
Third-Party Risk Management centralises onboarding, due diligence, periodic reviews, and exception tracking. Define flow-down requirements once and apply them at scale; request and version supplier artefacts automatically with Automated Evidence Collection. Dashboards highlight concentration risk by provider, region, and service, keeping DORA third-party obligations visible. |
|
Pillar 5: Information-Sharing Arrangements |
Document participation rules, approvals, and follow-up tasks in Compliance Management, then link resulting control updates (detections, configuration changes) as evidence with Automated Evidence Collection. Improvements from sector intelligence become measurable, repeatable, and auditable across all DORA pillars. |
Make DORA Operational
“In SureCloud, we’re delighted to have a partner that shares in our values and vision.”
Read more on how Mollie achieved a data-driven approach to risk and compliance with SureCloud.
“In SureCloud, we’re delighted to have a partner that shares in our values and vision.”
Read more on how Mollie achieved a data-driven approach to risk and compliance with SureCloud.
“In SureCloud, we’re delighted to have a partner that shares in our values and vision.”
Read more on how Mollie achieved a data-driven approach to risk and compliance with SureCloud.

Reviews
Read Our G2 Reviews
4.5 out of 5
"Excellent GRC tooling and professional service"
The functionality within the platform is almost limitless. SureCloud support & project team are very professional and provide great...
Posted on
G2 - SureCloud
5 out of 5
"Great customer support"
The SureCloud team can't do enough to ensure that the software meets our organisation's requirements.
Posted on
G2 - SureCloud
4.5 out of 5
"Solid core product with friendly support team"
We use SureCloud for Risk Management and Control Compliance. The core product is strong, especially in validating data as it is...
Posted on
G2 - SureCloud
4.5 out of 5
"Excellent support team"
We've been happy with the product and the support and communication has been excellent throughout the migration and onboarding process.
Posted on
G2 - SureCloud
Product +
Frameworks +
Capabilities +
Industries +
Resources +
London Office
1 Sherwood Street, London, W1F 7BL, United Kingdom
US Headquarters
6010 W. Spring Creek Pkwy., Plano, TX 75024, United States of America
© SureCloud 2026. All rights reserved.

.png)