Quick Links
- The 2026 DORA Enforcement Landscape
- What DORA Means for Banks
- What DORA Means for Fintechs
- What DORA Means for Insurers & Reinsurers
- Comparative Matrix: DORA 2026 Sector Impact
- Cross-Sector Trends Emerging for 2026
- How SureCloud Supports Each Sector
- Turn 2026 Supervision Into Day-to-Day Practice
- FAQs
What DORA Means for Banks, Fintechs & Insurers in 2026
As 2026 approaches, DORA moves from planning to supervision. Regulators are shifting from guidance to enforcement—standardizing major incident reporting, expanding threat-led testing where required, and tightening oversight of critical ICT third-party service providers (CTPPs). The expectation is clear: controls must run in practice—with evidence.
We’ll view the impact through three lenses—Banks, Fintechs, and Insurers—because the same rules create different pressure points: scale and legacy for banks, speed and vendor mix for fintechs, and data integrity and continuity for insurers.
In our Complete Guide to DORA Compliance, we explained the rulebook. Now we’ll focus on 2026 and what your sector should prioritize next.
These priorities apply across the DORA financial sector and will help teams working on DORA for banks, fintechs, and insurers focus effort where it counts.

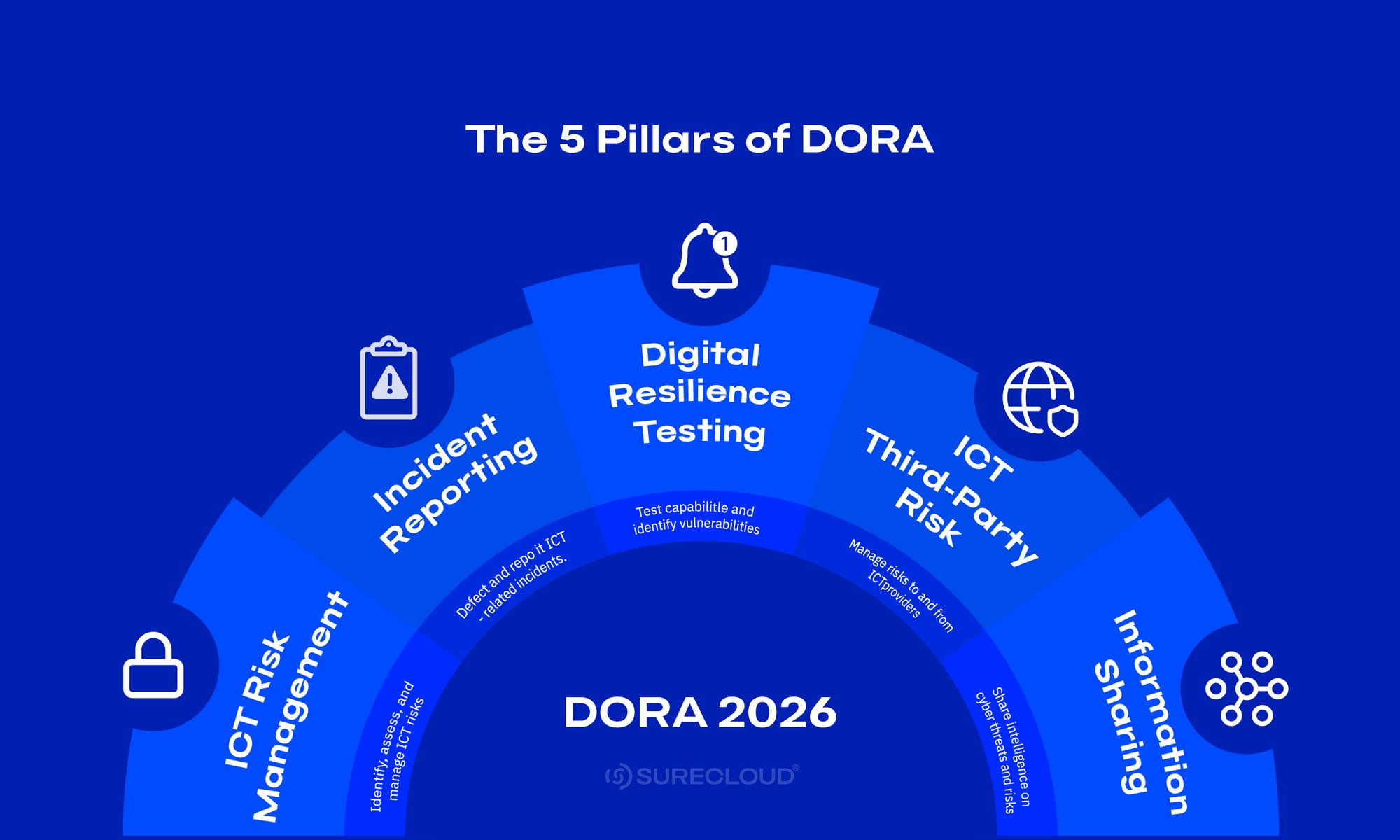
The 2026 DORA Enforcement Landscape
As the Digital Operational Resilience Act 2026 supervisory phase ramps up, authorities will focus on how well programs run, not just what’s written in policy.
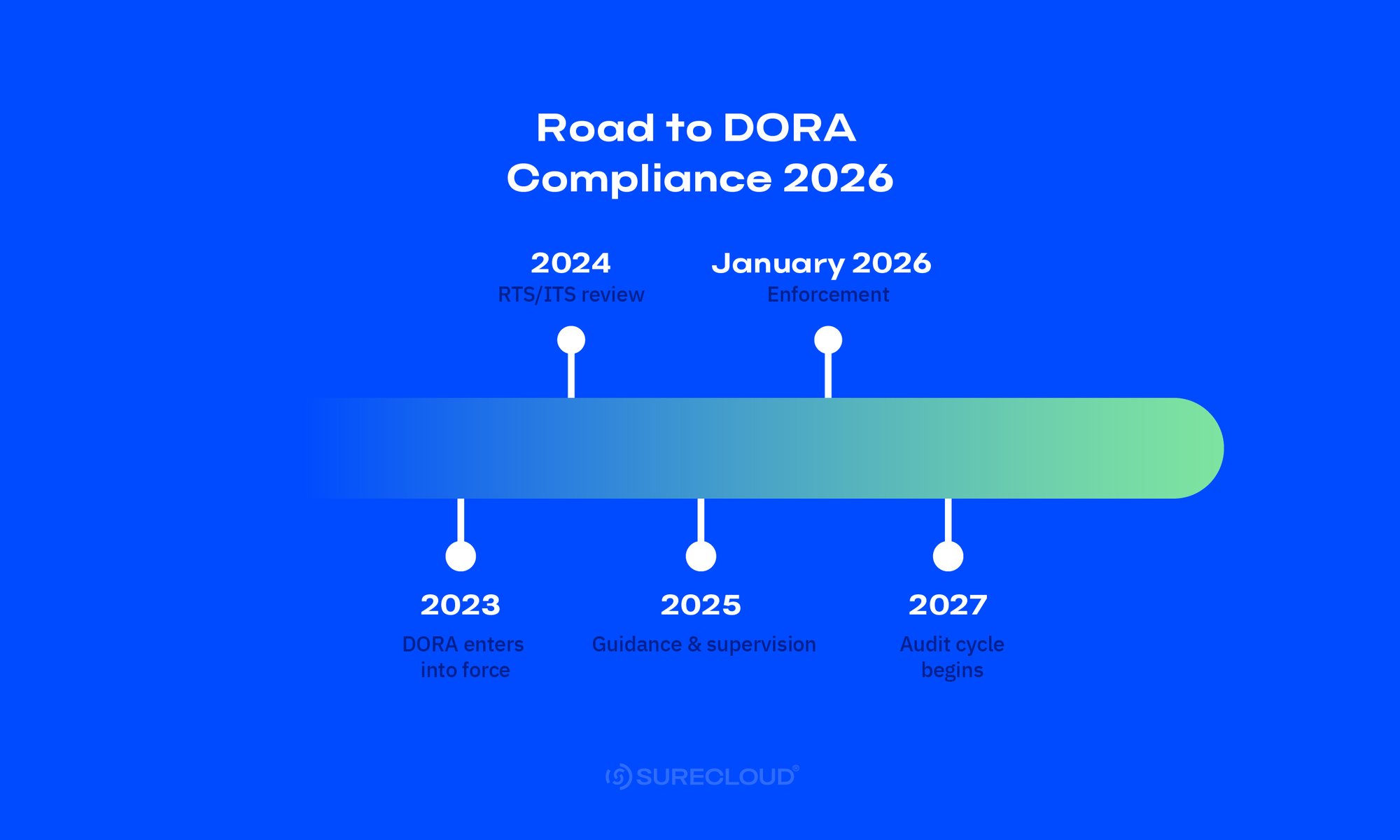
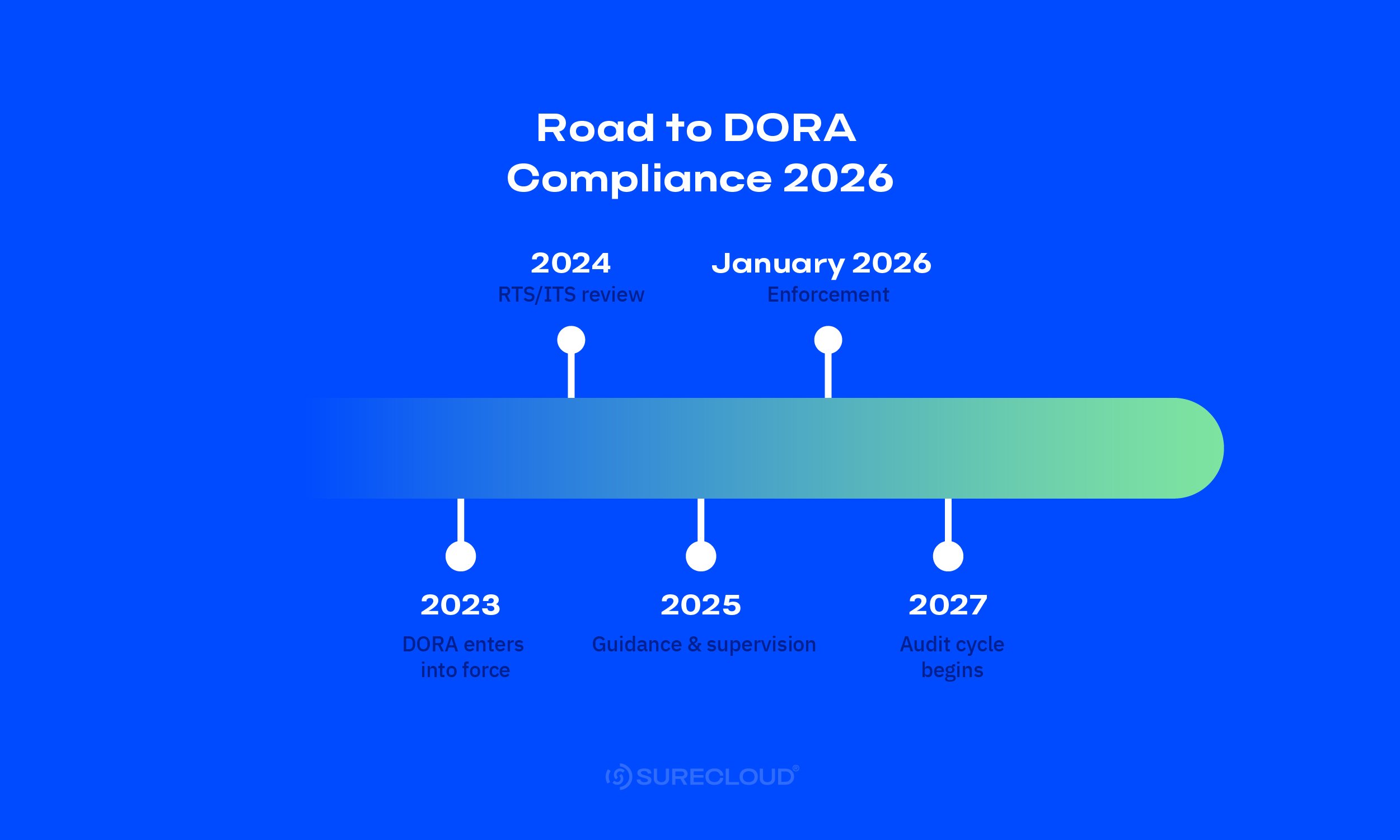
Key dates to anchor planning
January 2025 — DORA applies
In-scope firms must run ICT risk management, testing, incident reporting, and third-party oversight to the Act’s standard.
Mid-2026 — Supervisory activity ramps
Supervisory audits, sector stress testing, and data requests ramp as incident reporting Regulatory Technical Standards/Implementing Technical Standards (RTS/ITS) bed in and Threat-Led Penetration Testing (TLPT) aligns to the updated Threat Intelligence-based Ethical Red Teaming (TIBER-EU) framework.
Late-2026 — First fines and enforcement actions expected
With the oversight model operating and CTPPs under EU-level coordination, authorities are positioned to act where obligations aren’t met.
EU-level coordination: the Oversight Forum (OF)
DORA adds a pan-EU structure for supervising CTPPs. The Oversight Forum (OF), a standing committee of the European Supervisory Authorities (ESAs) Joint Committe, supports the Lead Overseer and Joint Examination Teams (JETs) so examinations and follow-up are coordinated across member states.
Roadmap signals from supervisors (EBA/ESMA 2025–2026)
Supervisory work programs point to this arc: finalize/operationalize RTS/ITS, scale TLPT, and tighten EU-level oversight of CTPPs—with more data-driven reviews through 2026.
Enforcement watchlist (what supervisors will look for)
- Incident data quality against RTS/ITS fields and timelines (initial, intermediate, final)
- TLPT designation and scope confirmation, with supplier participation where needed
- Contract controls for CTPP dependencies; flow-down obligations, evidence cadences, and exit/substitution terms for key CTPPs (DORA ICT providers)
What DORA Means for Banks
Where the pressure lands in 2026
Banks are likely to be first in line for supervisory reviews and inspections. They also carry the most scale and interdependence. That raises expectations on three fronts: a single, accurate register (services, systems, data, suppliers), programmatic testing (baseline year-round and TLPT if designated), and incident reporting that uses standard fields and timelines.
What to prioritize now
- Finish the register: Include owners, criticality, dependencies, and key third parties. Keep it live.
- Publish a 12-month test plan: Tie each test to the control it proves and schedule retests. Include backup/restore and failover drills with documented outcomes.
- Align incident workflows to the EU model: Use the same fields and timelines your authority expects (initial, intermediate, final) to improve reporting accuracy.
- Tighten supplier terms: Flow-down incident cooperation, testing support (including TLPT participation), resilience outcomes, reporting/audit rights, and exit/substitution.
Common pitfalls
- Parallel spreadsheets for assets and suppliers (data drifts, owners unclear).
- “Point-in-time” tests with no retest after fixes.
- Incident forms that don’t match required fields, forcing rework in the first 24 hours.
- Cloud contracts without clear evidence cadences or outage/restore reporting
What evidence lands well
- The register, exported with owners and last-updated dates.
- A test calendar with status, findings, and closed/retested items.
- Sample incident packs showing timestamps, facts, actions, and approvals.
- Supplier artifacts on a schedule (certs, pen-test summaries, recovery drills, uptime/incidents).
Alignment note
Map once, prove once: align DORA controls with EBA expectations, Basel III principles on operational resilience, and ISO/IEC 27001 control families to reduce duplication—a practical way to make DORA for banks operational rather than project-based.
Sector Example: Dora for Banks
A Tier 1 EU bank runs a single service-based register with CTPP flags and RTO/RPO owners, files RTS/ITS-aligned incident packs on the clock, and keeps a TLPT dossier with supplier sign-off and scheduled retests
What DORA Means for Fintechs
Where the pressure lands in 2026
Fintech teams are lean, but the bar is the same. Rapid growth increases exposure to ICT and data risk; multi-cloud/SaaS adds dependencies; audit maturity can lag. The advantage is agility: build compliance by design with a compact control set, automated evidence, and RTS/ITS-ready incident forms. That’s the bar for DORA for fintechs in 2026.
What to prioritize now
- Stand up one register early: Capture services, systems, data, and vendors with owners and criticality
- Adopt a compact control set: Access, change/configuration, backup/restore, logging/monitoring, vulnerability, secure development; set cadence and retests
- Automate high-friction evidence: Access reviews, restore tests, and log exports should land in one place on a schedule
- Pre-align incident forms: Use the standard field names and the 4h/24h/72h/1-month timeline so analysts aren’t re-keying under pressure
- Harden contracts: Flow-down incident cooperation, reporting timelines, artifact delivery, and exit terms to key suppliers
Common pitfalls
- Treating “policy” as compliance, without proof the controls run
- Vendor sprawl with no cadence for artifact refreshes
- Missing owners for shared services (e.g., identity, logging)
- Incident timelines built ad hoc during an event
What evidence lands well
- A single control library mapped to DORA (and ISO where relevant), with owners and due dates
- A short, risk-based test plan tied to business services
- A standing incident evidence pack template (timeline → root cause → impact → recovery → lessons)
- Vendor files that refresh automatically (certifications, test summaries, uptime/incidents, sub-processors)
Why this matters
Early alignment with DORA can become a competitive differentiator in bank partnerships and licensing.
Sector Example: Dora for Fintechs
A licensed fintech maintains a compact DORA ↔ ISO 27001 control library with named owners, automates evidence pulls for access reviews, restore tests, and logs, and ships a standing due-diligence pack for bank partners and supervisors

What DORA Means for Insurers & Reinsurers
Insurance runs on data integrity and continuity. DORA therefore focuses attention on underwriting, pricing, and claims platforms; group structures with many entities; and the third parties in the middle (TPAs, adjusters, analytics providers). This sits alongside the European Insurance and Occupational Pensions Authority (EIOPA) expectations and intersects with Solvency II on operational resilience and continuity. These are the essentials of DORA for insurers.
What to prioritize now
- Map the data path: Trace how policy, pricing, and claims data move across systems and entities; mark single points of failure
- Prove recovery: Set Recovery Time Objective (RTO) / Recovery Point Objective (RPO) for actuarial and claims systems and evidence successful restores/failovers on a cadence
- Harmonize the playbook: Align incident fields and timelines across IT, claims, and operations so the 4h/24h/72h/1-month flow runs end-to-end
- Tighten third-party oversight: Flow-down incident cooperation, drill participation, data handling, and evidence delivery to TPAs and analytics vendors
Common pitfalls
- Local teams keep separate asset/supplier lists; group has no single view
- Backups exist, but restore tests are irregular or undocumented
- Incident timelines sit in email threads; evidence collection starts too late
- Third-party adjusters aren’t on the same reporting clocks or data fields
What evidence lands well
- A group-level register with owners, criticality, and dependencies (by entity)
- Restore/failover drills with timestamps, results, approvals, and retests
- A standard incident pack template used by IT and claims
- Supplier artifacts on schedule (certifications, pen-test summaries, recovery drill outputs, uptime/incidents, sub-processors)
Sector Example
A pan-European insurer keeps a group view of underwriting, pricing, and claims with owners and RTO/RPO, runs scheduled restore and failover drills across entities, and standardizes an RTS/ITS-aligned incident form for fast supervisor requests
Comparative Matrix: DORA 2026 Sector Impact
How to use this matrix
Use this at-a-glance view to brief owners on what matters most in 2026 by sector.
|
Sector |
Oversight Level |
Complexity |
Primary Focus |
Key 2026 Challenge |
|
Banks |
High |
High |
ICT Risk Management & Resilience Testing |
Demonstrating full lifecycle governance |
|
Fintechs |
Moderate |
Variable |
Vendor Oversight & Data Controls |
Scaling compliance fast with limited resources |
|
Insurers |
Moderate |
Medium |
Data Integrity & Continuity |
Cross-border compliance and dependency mapping |
Cross-Sector Trends Emerging for 2026
- Increased regulator collaboration: EU oversight of CTPPs is becoming more coordinated via the Oversight Forum (OF), the Lead Overseer, and Joint Examination Teams (JETs)—expect tighter information-sharing and more consistent follow-up
- Rise of ‘RegTech resilience’: Teams are adopting platforms (e.g., SureCloud) to centralize evidence, map once across DORA/ISO/NIS2, and reuse proof in audits and supervisory reviews
- Continuous testing culture: Baseline (year-round) resilience testing becomes business-as-usual (BAU); TLPT applies to designated firms, often on a multi-year cadence set by the TLPT authority
- Vendor accountability expansion: Shared risk documentation and flow-down obligations extend across the supply chain—cloud, SaaS, payments, analytics—so third-party proof lands on time and in a standard format (including DORA ICT providers' obligations)
How SureCloud Supports Each Sector
SureCloud turns governance intent into execution: one register, one control library, automated evidence, and regulator-ready reporting.
Banks
- Integrate existing frameworks with DORA in one control library; assign owners, cadence, and retests
- Automate evidence for access reviews, logging/monitoring, backup/restore, and change—keep a versioned audit trail
- Coordinate baseline and TLPT tasks on a single plan with dashboards that surface overdue actions and exceptions
- Automated reporting dashboards for regulators. Produce regulator-ready packs aligned to standard incident fields, testing status, and supplier evidence
Fintechs
- Quick-start templates for resilience policies. Launch a compact, risk-based control set without overbuilding
- Evidence automation for audits and vendor due diligence. Capture access reviews, restore tests, logging, and supplier artifacts on schedule—ready for bank partners and supervisors pursuing fintech DORA readiness
Insurers
- Risk and continuity mapping for actuarial systems. Trace dependencies across underwriting, pricing, and claims; attach restore/failover evidence
- Multi-entity control alignment and cross-border tracking. Standardize controls, owners, and exceptions across subsidiaries for consistent proof
Turn 2026 Supervision Into Day-to-Day Practice
As the Digital Operational Resilience Act (DORA) enters its 2026 supervisory phase, shift from projects to cadence. Keep one register. Map controls once. Test continuously and run TLPT if designated. Align incident reporting to standard fields and timelines. Keep supplier evidence current. Proactive beats reactive. It lowers audit friction and protects delivery.
“In SureCloud, we’re delighted to have a partner that shares in our values and vision.”
Read more on how Mollie achieved a data-driven approach to risk and compliance with SureCloud.
Frequently Asked Questions
What does DORA mean for banks?
Banks should expect closer supervision in 2026, with emphasis on a single, accurate register, programmatic testing (baseline year-round and TLPT if designated), and incident reporting aligned to standard fields and timelines.
Does DORA apply to fintechs?
Yes. Fintechs must meet the same resilience standard as banks. A compact control set, automated evidence, and RTS/ITS-ready incident forms make it achievable with lean teams.
How does DORA affect insurers?
DORA covers ICT that supports underwriting, pricing, and claims. Supervisors will look for data integrity, restore/failover evidence, and consistent group-level control operation.
Ready to Comply?
Here’s Your Next Step
As DORA enforcement ramps up, readiness can’t wait. Whether you’re a bank aligning registers and tests, a fintech building compliance by design, or an insurer harmonising continuity evidence, SureCloud helps turn frameworks into proof. Explore how SureCloud simplifies DORA compliance for your sector and prepares you for 2026 supervision.

.png)