DORA Compliance Roadmap:
Process, Timeline & Milestones
DORA has officially been in action since January 17, 2025, and enforcement has begun. Through 2026, supervisors are moving from guidance to inspections, data requests, and (where designated) Threat-Led Penetration Testing (TLPT)—with EU-level oversight of critical ICT third-party providers (CTPPs) maturing into 2027.
This article is your DORA compliance roadmap—a strategic implementation guide that sequences the work, the order you’ll do it in, and the proof you’ll produce at each step.
In our Complete Guide to DORA Compliance, we outlined what the regulation requires. Here, we show how to get there—step by step with a six-stage DORA implementation plan, clear owners and schedule, and evidence packages ready for review. Run it as a repeatable DORA compliance process—and keep the cadence steady.

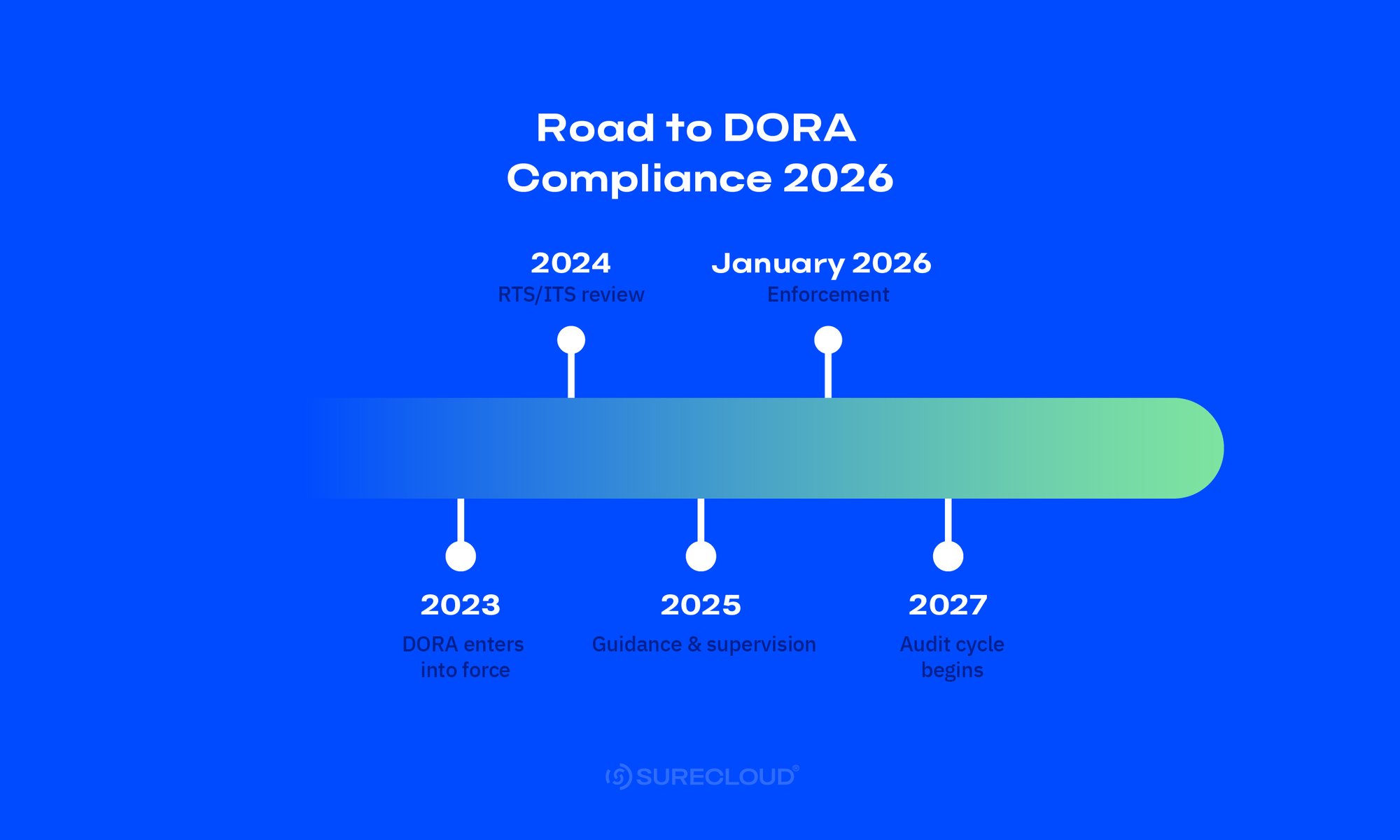
DORA Compliance Timeline (2023–2027): What Happens When
DORA applies from January 17, 2025, with supervision ramping through 2026 and EU-level oversight of CTPPs maturing in 2027. Use this Digital Operational Resilience Act timeline to align regulatory dates with your internal checkpoints.
Tip: Refer back to your DORA compliance timeline at each quarterly checkpoint so owners, tests, and evidence stay on schedule.
Recap: Key Legislative Milestones
- 2022: Regulation (EU) 2022/2554 adopted and published
- January 16, 2023: Regulation enters into force
- January 17, 2025: DORA applies to in-scope financial entities
Highlight: Dora Enforcement in 2026 & Upcoming Phases
- 2025: Supervisory posture builds, major-incident reporting model, and baseline testing cadence established
- 2026: Supervisory reviews and inspections ramp, sector exercises, and TLPT where designated
- 2027 and beyond: EU-level oversight of CTPPs in steady state with recurring testing and evidence cycles

The DORA Compliance Roadmap:
Six Stages
Use these stages as a DORA implementation plan with owners, inputs, outputs, and a steady cadence of proof. Each stage includes an at-a-glance DORA compliance checklist so teams know what “done” looks like.
Stage 1: Assess & Inventory
Goal: Establish a single picture of critical business services, systems, data, and third parties so risk, testing, and incident processes attach to reality.
Inputs:
- Business services and critical functions
- System and data maps
- Third-party and subcontractor list
- Prior audits, incidents, and continuity documents
Work to complete:
- Build one consolidated register keyed by business service with owners, criticality, RTO/RPO targets, data classification, and CTPP flags
- Map supply-chain dependencies, including subcontractors and concentration points
- Identify documentation and evidence gaps so later stages can close them
Outputs:
- Current-state register with coverage level and last-updated dates
- Service dependency diagrams that expose single points of failure
- Gap list tied to later stages in this roadmap
Checklist:
- Services, systems, data, and vendors in one register
- Owners and criticality assigned and visible
- CTPPs and subcontractors flagged consistently
- RTO/RPO captured for critical services
Stage 2: Build Governance & Control Framework
Goal: Define how DORA is run day-to-day with roles, committees, policies, and a control library so everyone knows who does what and which controls prove compliance.
Inputs:
- Register and dependency maps
- Existing policy set and frameworks such as ISO/IEC 27001 and NIS2
- Board and risk committee structures
Work to complete:
- Create a DORA control library mapped to Articles and to RTS/ITS fields where appropriate
- Define governance such as roles, oversight committees, escalation paths, and KRIs/KPIs
- Establish evidence cadences and an exceptions process so findings don’t stall
Outputs:
- Operating model document with RACI for DORA activities
- Control library mapped to DORA and reused across ISO/IEC 27001 and NIS2 to limit duplication
- Calendar for evidence, committee reviews, and control testing
Checklist:
- Control owners and testing frequencies set
- Evidence cadences defined and automated where possible
- RACI for incident reporting, testing, and supplier oversight
- Cross-map to ISO/IEC 27001 and NIS2 to avoid duplicate work
Stage 3: Map Risk Management & Testing
Goal: Run risk and testing as a closed loop so you assess, test, fix, and retest while keeping proof current.
Inputs
- Control library and risk register
- Prior exercises, test results, and incidents
- Business impact analyses and recovery expectations
Work to complete:
- Establish baseline testing calendars across access, backup/restore, logging, change, vulnerability, and continuity
- Prepare for Threat-Led Penetration Testing (TLPT) if designated, scoped to TIBER-EU conventions, with supplier participation letters agreed in advance where needed
- Track findings, fixes, and retests on one plan so nothing goes stale
Outputs
- Annual test plan aligned to business services and control objectives
- TLPT scoping memo and timeline if designated by your authority
- Closure reporting with before/after evidence and dates
Checklist:
- Baseline tests scheduled and linked to controls
- Findings tracked to closure with retest dates
- TLPT preparation in place if designated
- KPIs on test coverage and time-to-retest
Stage 4: Align Incident Reporting to RTS/ITS
Goal: Make incident reporting accurate and on time using the Joint Regulatory Technical Standards (RTS) and Implementing Technical Standards (ITS) model for major-incident reporting so the first 24–72 hours are smooth, not chaotic.
Inputs:
- Incident playbooks and tooling
- ESAs RTS/ITS data fields and timelines
- Escalation matrices and on-call rotas
Work to complete:
- Mirror RTS/ITS fields in intake forms and response tooling
- Implement the 4h initial notification (after classification and ≤24h from detection), 72h intermediate, and 1-month final pattern
- Build a model incident evidence pack with timestamps and approvals
- Train responders and run tabletop drills with compliance observers
Outputs:
- Standard incident forms and a model evidence pack
- Time-stamped drills demonstrating on-time reporting
- Clear escalation and approval steps
Checklist:
- Intake forms match ESAs fields and clocks
- Evidence packs ready before incidents happen
- Weekend and holiday handling defined
- Training and tabletop exercises logged
Stage 5: Strengthen Third-Party & CTPP Oversight
Goal: Prove shared accountability with critical suppliers through contracts, evidence, and exit options so risk doesn’t bottleneck in your supply chain.
Inputs:
- Vendor inventory and risk tiers
- Contracts, SLAs, disaster recovery terms, and audit rights
- Incident and testing cooperation clauses
Work to complete:
- Add flow-down clauses for incident cooperation, drill participation, reporting timelines, artifact delivery, and right-to-audit
- Set a supplier evidence calendar and automate collection where possible
- For CTPPs, ensure oversight expectations align with the Lead Overseer and JETs model at EU level
Outputs:
- Evidence bundles per critical vendor
- Contract addenda or playbooks to operationalize obligations
- Exit and substitution plan for high-exposure services
Checklist:
- Flow-down obligations in place
- Evidence cadences set and tracked
- Exit strategy documented and tested for high-impact services
- CTPP oversight mapped to the EU model
Context:
EU-level oversight of CTPPs is coordinated by the ESAs’ Oversight Forum (OF) (a Joint Committee sub-committee), supporting the Lead Overseer (LO) and Joint Examination Teams (JETs).
Stage 6: Prove & Improve
Goal: Make evidence and improvement the default so audits and supervisory reviews are repeatable and quick.
Inputs:
- Evidence generated in Stages 1–5
- Dashboards, KPIs/KRIs, and exception queues
- Audit findings and management actions
Work to complete:
- Produce a consolidated DORA program pack for leadership and regulators
- Trend coverage, exceptions, time-to-fix, and time-to-retest so progress is visible
- Fold lessons from incidents and tests back into the register, controls, and contracts
Outputs:
- Executive and regulator-ready reporting
- Trending that shows resilience improving over time
- Updated roadmap for the next two quarters
Checklist:
- One source of truth for evidence and status
- Trends and exceptions visible to owners and leadership
- Next quarter’s plan agreed and resourced
Duration & Effort by Organization Type (SME vs Enterprise)
Different organizations move at different speeds. Use these example DORA project milestones to set expectations.
SME Pattern
These DORA project milestones help SMEs stage the work without overbuilding
- 0–30 days
- Stand up the register and owners
- Approve a lean control set and evidence cadence
- 31–90 days
- Baseline tests live with findings and retests
- Incident forms aligned to RTS/ITS and a model evidence pack drafted
- Supplier evidence calendar launched
- 91–180 days
- First cycle of tests closed with retests completed
- Contract addenda prepared for high-importance vendors
- Program pack prepared for leadership
Enterprise Pattern
- 0–60 days
- Consolidate registers and dependency maps across divisions
- Establish a single control library and governance forums
- 61–150 days
- Baseline testing program running across critical services
- TLPT scoping underway if designated
- Incident forms, clocks, and drill evidence standardized across teams
- 151–270 days
- Supplier flow-down and evidence cadence implemented with dashboards
- Group-level reporting pack and trends live for leadership and regulators
- Independent assurance review (internal/external) scheduled for selected controls
Duration & Effort by Organization Type (SME vs Enterprise)
Use this crosswalk to show how your roadmap operationalizes the regulation’s working parts.
![]()
Read more about the 5 pillars of DORA in our detailed guide.

- ICT Risk Management → Stages 1–3 assess inventory, build the control library, and schedule baseline tests and retests
- Incident Reporting → Stage 4 mirror RTS/ITS fields and clocks in forms, drills, and evidence packs
- Resilience Testing → Stages 3 & 6 run baseline testing year-round and TLPT where designated, then track fixes through to retest
- Third-Party Risk → Stage 5 add flow-down clauses, set evidence calendars, and prepare exit/substitution for critical suppliers
- Information Sharing → Stage 6 standardize templates and legal guardrails for sector sharing arrangements

Roles, Ownership & Operating Rhythm
Who does what:
- Program owner and steering forum
- Control owners and process owners
- Incident commander and compliance approvals
- Supplier managers and legal for flow-down
- Internal audit liaison for independence and evidence checks
Operating rhythm:
- Monthly:
- Control status review and exception triage
- Supplier artifact review for those due
- Quarterly:
- Retest closure check and trend review
- Report to leadership and update the roadmap
- Annually:
- Program refresh against latest RTS/ITS guidance and sector notes
- TLPT readiness check or scoping if designated
Risks, Pitfalls & How to Avoid Rework
Common traps to avoid:
- Parallel inventories that never match
- Tests without retests to prove fixes
- Incident forms that don’t match RTS/ITS fields or clocks
- Vendor artifacts without a cadence or owner
- No exit or substitution plan for critical suppliers
Controls that prevent rework:
- One register and one control library
- A single master calendar for testing, incidents, and supplier evidence
- Standard evidence packs per scenario
- Exception queues with owners and due dates
How SureCloud Accelerates Your DORA Implementation
This is how teams use SureCloud to convert policy into repeatable operations.
Unified register and control library
- One place to define services, systems, data, owners, criticality, and CTPP flags
- Map controls centrally and reuse across DORA, ISO/IEC 27001, and NIS2
Testing and TLPT orchestration
- Schedule baseline tests, track findings to retest, and manage TLPT tasks if designated
- Dashboards show coverage, exceptions, and time-to-retest
Incident reporting aligned to RTS/ITS
- Configurable forms mirror ESAs fields and clocks so the 4h / ≤24h / 72h / 1-month cadence is built into the workflow
- Evidence packs with timestamps and approvals remain versioned and audit-ready
Third-party and CTPP oversight
- Flow-down obligations, artifact calendars, and exit plans tracked in one place
- Vendor risk posture and evidence freshness visible at a glance
Automated evidence collection and reporting
- Pull artifacts on a schedule from your document sources
- Generate leadership and regulator-ready packs on demand
Frequently Asked Questions
What are the stages of the DORA compliance process?
Assess and inventory, build governance and a control library, run risk and baseline testing with retests, align incident reporting to RTS/ITS, strengthen third-party and CTPP oversight, and prove and improve through trending and updates.
How long does DORA compliance take?
SMEs often reach steady cadence in 3–6 months for a well-scoped program, while enterprises take 6–9 months to consolidate registers, harmonize forms, and scale testing, with multi-year TLPT rhythms set by authorities for designated entities.
What’s changing in 2026?
More supervision, more data requests, and deeper testing for designated firms under TLPT, plus coordinated oversight of CTPPs through the EU model.
From Roadmap to Results
A strong DORA compliance roadmap orders the work and the evidence. Run the six stages as a loop. Assess and inventory, build governance, test and retest, align incident reporting to RTS/ITS, raise assurance over critical suppliers, and fold lessons into the next cycle. That’s how you convert policy into repeatable operations, reduce audit overhead, and stay aligned with 2026 supervisory expectations.
Read more from the SureCloud DORA Compliance Hub
"Excellent support team" We've been happy with the product and the support and communication has been excellent throughout the migration and onboarding process.
G2 - SureCloud
"Excellent support team" We've been happy with the product and the support and communication has been excellent throughout the migration and onboarding process.
G2 - SureCloud
"Excellent support team" We've been happy with the product and the support and communication has been excellent throughout the migration and onboarding process.
G2 - SureCloud
"Excellent support team" We've been happy with the product and the support and communication has been excellent throughout the migration and onboarding process.
G2 - SureCloud
"Excellent support team" We've been happy with the product and the support and communication has been excellent throughout the migration and onboarding process.
G2 - SureCloud
.png)








_HighPerformer_Enterprise_HighPerformer.png)








