Quick Links
- What Is a DORA Audit or Supervisory Review?
- Step 1: Conduct a Self-Assessment
- Step 2: Build Your Audit Evidence Library
- Step 3: Engage Internal Stakeholders
- Step 4: Prepare for Regulator Question
- Step 5: Simulate and Improve
- 90-Day Plan to Audit-Ready
- Sample Lists You Can Use
- FAQs
- How SureCloud Supports DORA Audit Readiness
How to Prepare for a DORA Audit or Supervisory Review
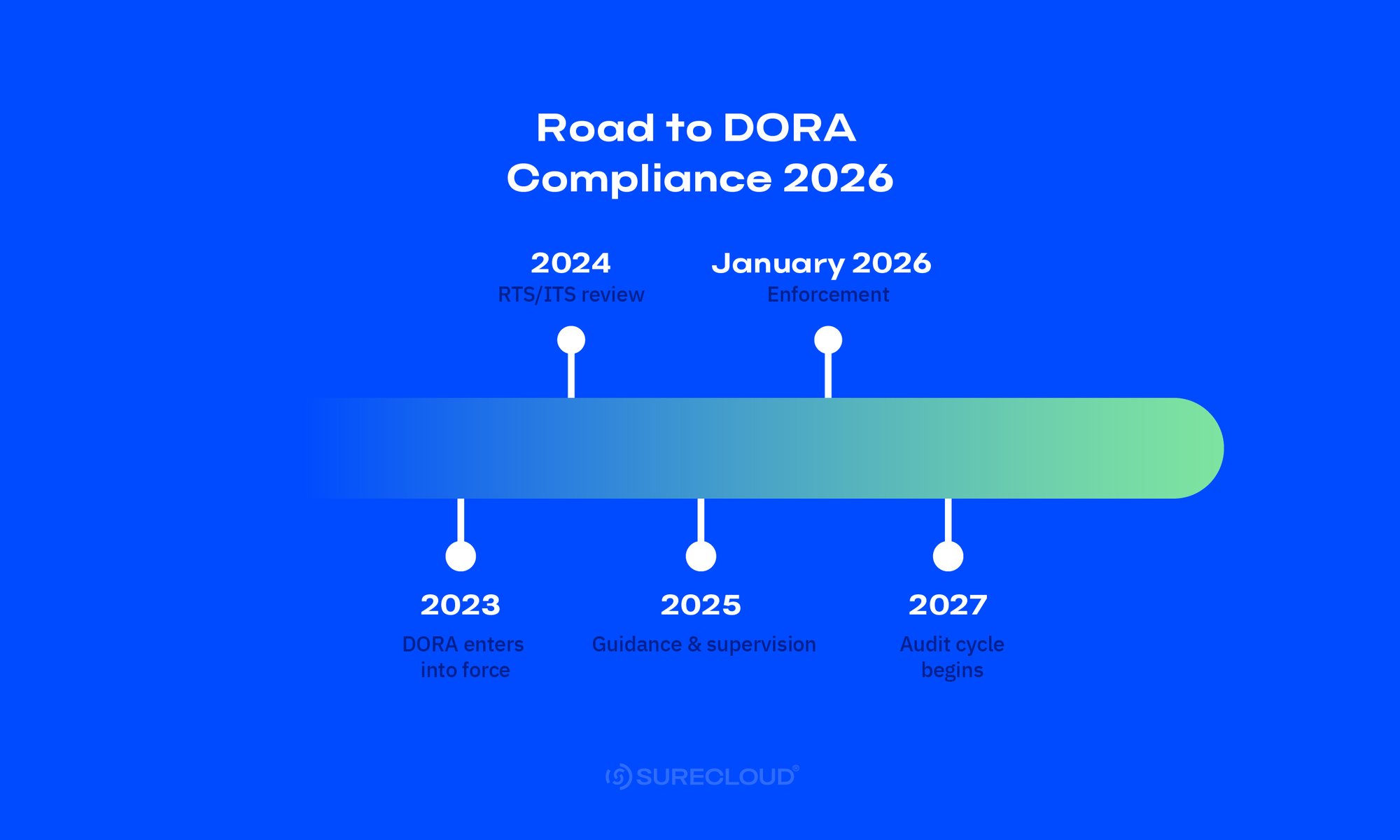
DORA has applied since January 17, 2025. Through 2026, supervisors are shifting from guidance to inspections, data requests, and—where designated—TLPT, while EU-level oversight of critical ICT third-party providers (CTPPs) scales into 2027.
If you’re planning DORA audit preparation, the goal is simple — be ready on any day, not just audit day.
This article is your practical DORA supervisory review playbook. We explain how reviews are organized, which documents and proofs examiners expect, how to structure owners and a clear operating cadence, and how to run internal mock reviews so gaps surface early and close fast. For regulatory foundations and scope, see our DORA Compliance Guide and Understanding DORA, then use this piece to operationalize audit readiness step by step.
Who This Applies To:
- Financial entities regulated under EU financial services law
- ICT providers impacted through flow-down obligations and, if designated as CTPPs, via EU-level oversight
What Is a DORA Audit or Supervisory Review?
A DORA (Digital Operational Resilience Act) audit or DORA supervisory review is a regulatory examination of how your organization meets DORA’s operational resilience duties in practice. It is not ISO certification and not just an internal audit. Examiners look for live processes, tested controls, and traceable evidence that match the regulation’s requirements.
Who Conducts It
- Your National Competent Authority executes the review locally — examples include BaFin in Germany, Banque de France/ACPR in France, and the Central Bank of Ireland (CBI) in Ireland
- The European Supervisory Authorities (ESAs) — EBA, ESMA, EIOPA — coordinate guidance and technical standards and support EU-level oversight for designated critical ICT third-party providers
What Examiners Assess
- ICT risk management and governance
- Incident response and reporting aligned to RTS/ITS fields and timelines
- Third-party oversight, including subcontractors and flow-down obligations
- Testing programs, including TLPT where designated
- Documentation completeness, versioning, and traceability
What Triggers a Review
- Routine supervisory cycle
- Thematic review across a peer set
- Follow-up on prior findings
- Post-incident examination
What to Expect from Supervision
EU DORA supervisory reviews mirror established EBA-style ICT examinations — a formal request list, documented controls tied to obligations, live evidence walkthroughs, and findings with dated actions.
Treat it like a structured ICT inspection, not a paperwork exercise.
Read on to see how to prepare for a DORA compliance audit or supervisory review..
Step 1: Conduct a Self-Assessment
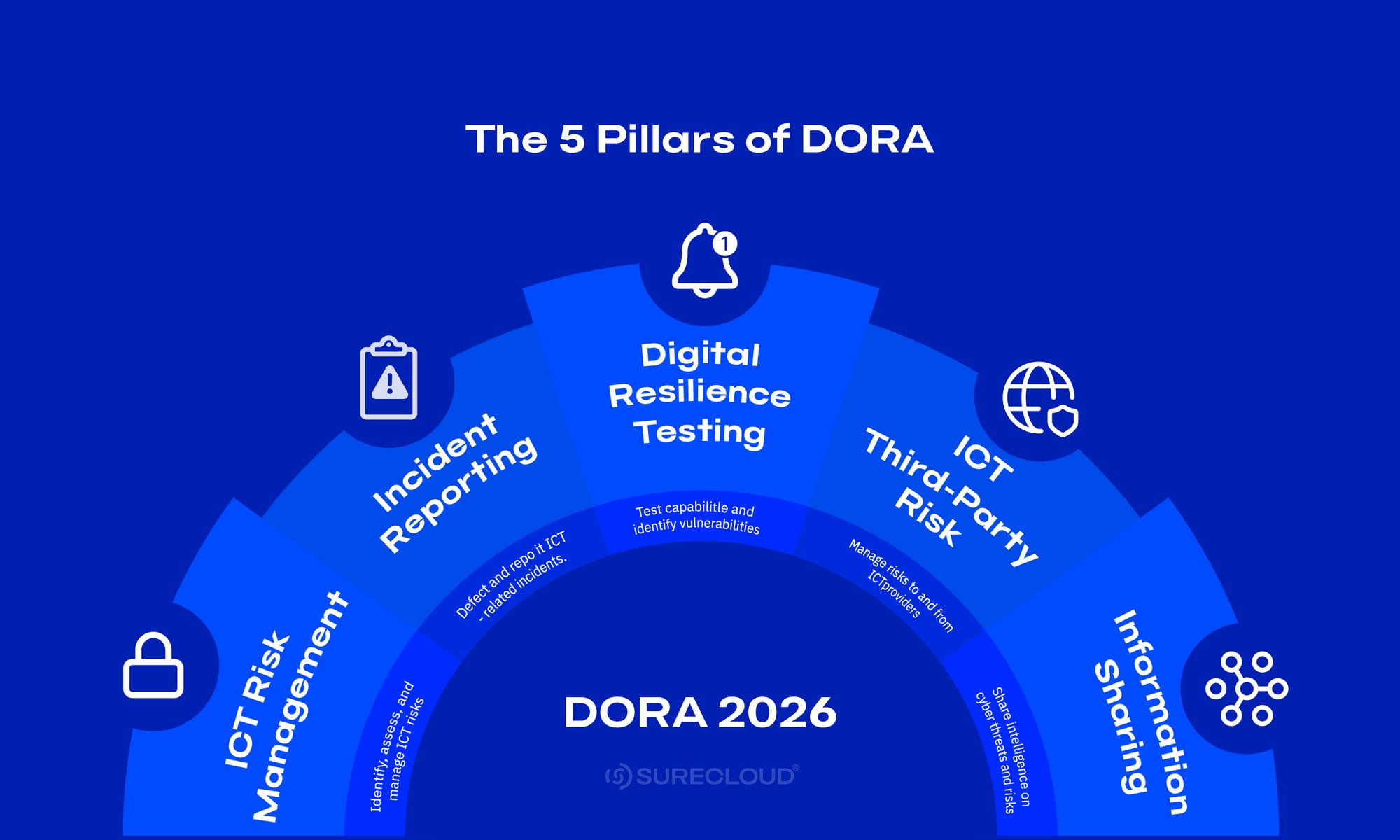
Run an internal gap analysis against DORA’s five pillars so you know where you stand before examiners arrive.
How to approach it
- Use the five pillars as your frame: ICT risk management, incident reporting, resilience testing, third-party risk, information sharing
- Perform a control-by-control check and capture gaps, owners, and due dates in your risk register
- Validate that testing calendars run year-round and include retests to prove fixes
- Confirm major-incident classification and report clocks are defined, rehearsed, and recorded
Validate with existing mappings
- Map your in-place controls to ISO/IEC 27001 Annex A where relevant
- Reuse NIS2 artifacts and processes where they meet the same DORA outcomes
- Record equivalence so auditors can trace each obligation to a live control and evidence
Mock-audit methodology
- Self-review against Annex I–IV with a regulator-style request list
- Walk through real incidents and tests, show artifacts live, and time each step
- Check traceability end-to-end: obligation → control → owner → evidence → last refresh
Checklist example excerpt
|
Area |
Verify |
Evidence examples |
Status |
Next action |
|
ICT governance |
Roles, committees, decision rights defined and active |
Governance charter, RACI, committee minutes |
On track |
Publish refreshed charter and RACI in Q4 |
|
Risk management |
Ongoing assessment with owners, treatment plans, KRIs/KPIs |
Risk register, risk appetite statement, mitigation actions |
In progress |
Close top risks and upload sign-offs |
|
Incident handling |
Classification logic, RTS/ITS fields in forms, clocks tested end-to-end |
Intake forms, drill logs, sample initial–intermediate–final report set |
Needs update |
Align forms to RTS/ITS clocks and rehearse 4h / ≤24h / 72h / 1 month flow |
|
Resilience testing |
Annual test plan active, findings tracked, retests completed |
Test plan, results, retest proof with timestamps |
On track |
Schedule retests for open high-risk findings |
|
Third-party oversight |
Tiering in place, artifacts calendarized, exit and substitution options |
Vendor register, SLAs, flow-down clauses, evidence calendar |
At risk |
Add subcontractor disclosure and right-to-audit to top-tier contracts |
Document outcomes from the DORA assessment in your risk register and track owners and due dates on a cadence.
Step 2: Build Your Audit Evidence Library
Supervisors expect traceable, verifiable evidence for every obligation. Centralize it so requests are answered quickly and consistently.
Recommended categories
- Policies & Procedures: Risk management, incident response, outsourcing and third-party rules, change management
- Registers & Logs: Vendors and subcontractors, incidents, assets, vulnerabilities
- Reports: Risk reviews, test results and retests, board and committee packs
- Records & Proof: Meeting minutes, approvals, system exports, screenshots, tickets, version histories
Make it exam-ready
- Tag each artifact to the obligation and control it proves, with an owner and refresh cadence
- Keep version history and snapshot sets before major changes
- Pre-assemble a model incident evidence pack with timestamps, approvals, and draft reports
Keep a simple, category-based layout that mirrors request lists and how teams work, so every artifact maps to a control and the relevant RTS/ITS field.
.jpg?width=800&height=480&name=dora-readiness-maturity-model%20(1).jpg)
Step 3: Engage Internal Stakeholders
Create an internal coordination model so requests, walkthroughs, and follow-ups run smoothly.
Build the audit coordination team
- Risk and Compliance as overall coordinators and owners of the request log
- IT and Security as technical SMEs for controls, testing, and tooling
- Legal for regulatory interpretation and escalation thresholds
- Procurement for contract artifacts and flow-down obligations
- Business owners for service impacts, continuity assumptions, and approvals
- Internal Audit for independent challenge and mock reviews
Clarify ownership and communications
- Single point of contact for the regulator and a clear backup
- Named evidence custodians per pillar with ready-to-show folders
- A live request tracker with status, owner, and due date
- A scribe to capture commitments, actions, and timestamps during meetings
- An escalation path for overdue items and blockers
Prepare briefing materials for each pillar
- One-page summary of obligations and how you meet them
- Control map references to policies, procedures, and technical controls
- Key artifacts list with location, owner, and last refresh
- Open issues with owners, due dates, and planned retests
- Short demo scenarios you can walk through live
- Talking points and handoffs so SMEs answer consistently
Step 4: Prepare for Regulator Question
Supervisors test how your program runs in practice, not just whether documents exist.
Sample DORA audit questions
- How is your ICT risk framework integrated with enterprise risk management?
- Show us your incident classification logic.
- When did you last test critical system failovers?
- Which ICT providers are classed as critical and why?
How to answer well
- Keep answers short and show the artifact live
- Reference the control ID and, where relevant, the RTS/ITS field it satisfies
- Point to time-bound outcomes such as test dates, findings, and retests
- Name the accountable owner and the next scheduled refresh
- Log any remediation as a dated action during the session
Step 5: Simulate and Improve
Run a realistic rehearsal so you can produce clean, complete evidence on demand.
Run a mock supervisory review
- Use Internal Audit or an external specialist to issue a regulator-style request list
- Recreate the end-to-end flow: intake, evidence collection, walkthroughs, findings, actions
- Time every stage so you know where delays occur and who unblocks them
- Score each area on evidence quality, not just policy presence
Verify reporting clocks in practice
- Confirm when the clock starts for a major incident and who authorizes the classification
- Prove your reporting cadence works under pressure — initial within 4 hours after classification and ≤24 hours from detection, intermediate at 72 hours, final at 1 month
- Check weekends and holidays do not break your timing model
- Validate draft fields match RTS/ITS templates so data is reusable
Close gaps and keep evidence fresh
- Assign owners and due dates for each finding and remediation
- Schedule retests to show closure and attach proof to the original finding
- Update policies, procedures, and registers and capture version history
- Snapshot the before/after evidence set so improvements are visible
90-Day Plan to Audit-Ready
Use this as a planning model. Adapt durations to your size and complexity.
Days 0–15
- Confirm scope, owners, and the operating rhythm
- Stand up the consolidated register for services, systems, data, and vendors
- Align incident forms to RTS/ITS fields and clocks
Days 16–30
- Populate the evidence library and assign refresh cadences
- Publish the annual test plan and schedule retests for open findings
- Identify critical suppliers and required flow-down updates
Days 31–60
- Run the first incident tabletop and a continuity drill
- Launch supplier evidence collection on a calendar
- Prepare TLPT scoping notes if designated by your authority
Days 61–90
- Execute a mock review with a realistic request list
- Close high-risk remediation items and snapshot updated evidence
- Produce an executive pack with status, gaps, and next-quarter actions
Sample Lists You Can Use
Model Incident Evidence Pack
- Incident summary including classification and start-clock decision
- Timeline with key timestamps and approvals
- RTS/ITS-aligned initial, intermediate, and final report drafts
- Root-cause notes and impact assessment
- Evidence of user or service notifications where required
- Follow-up actions with owners and due dates
- Links to logs, screenshots, and ticket history
Typical Regulator Request List
- Governance charter, RACI, and committee minutes
- Risk register with KRIs/KPIs and treatment plans
- Annual test plan, results, and retests
- Incident intake forms and model evidence pack
- Vendor register, tiering, SLAs, flow-down clauses, and artifact calendar
- TLPT scope memo if designated and evidence of finding closure
- Reporting pack for leadership with trends and exception queues
How SureCloud Supports DORA Audit Readiness
Centralize what matters and automate the admin so your team can focus on substance.
Centralize documentation and evidence
- One place for policies, registers, reports, and records with consistent tagging to obligations and controls
- Owner, refresh cadence, and last-updated date on every artifact
- Version history and snapshots you can export for exam packs
Use workflows for incident reporting and vendor tracking
- Configurable forms mirror RTS/ITS data fields and clocks so the 4h / ≤24h / 72h / 1 month timeline is built into the workflow
- Third-party flow-down obligations, evidence calendars, and audit rights tracked in one place
- Supplier due diligence, contract clauses, and renewal checkpoints in a single register
Automate reminders and generate audit-ready reports
- Automated reminders for review cycles, evidence refreshes, and retests
- Prebuilt dashboards and report packs for leadership and regulators drawn from the same source of truth
“In SureCloud, we’re delighted to have a partner that shares in our values and vision.”
Read more on how Mollie achieved a data-driven approach to risk and compliance with SureCloud.
Frequently Asked Questions
What is a DORA audit?
A DORA audit is a regulatory examination led by your National Competent Authority to verify that your organization meets DORA’s operational resilience obligations, with ESA-level guidance and standards coordinating approaches.
Who conducts DORA supervisory reviews?
National supervisors conduct the review locally, with coordination and common standards provided by the ESAs. For CTPPs, examinations are coordinated at EU level through a Lead Overseer and Joint Examination Teams, supported by the Oversight Forum.
How do I prepare for a DORA audit?
DORA audit preparation includes: Running a self-assessment, building an evidence library, setting ownership and a request-handling process, rehearsing with a mock review, and fixing gaps with dated retests so you can show progress at the next checkpoint.
What belongs in a DORA audit checklist?
Policies and standards, registers and logs, reports and analyses, records and proof, each tagged to a control and RTS/ITS field so it is traceable to an obligation.
Make Readiness the Operating Standard
Treat the DORA audit as an operating rhythm. Keep one evidence library, align incident forms to RTS/ITS, run testing and retesting on a cadence, and bring suppliers into scope with clear flow-down obligations and artifact schedules. That’s how you walk into a DORA supervisory review with confidence and leave with fewer findings and faster closure.

.png)