- ISO 27001
- 5th Nov 2025
- 1 min read
DORA vs NIS-2 vs ISO 27001: Where They Overlap & How to Combine Them

- Written by
In Short..
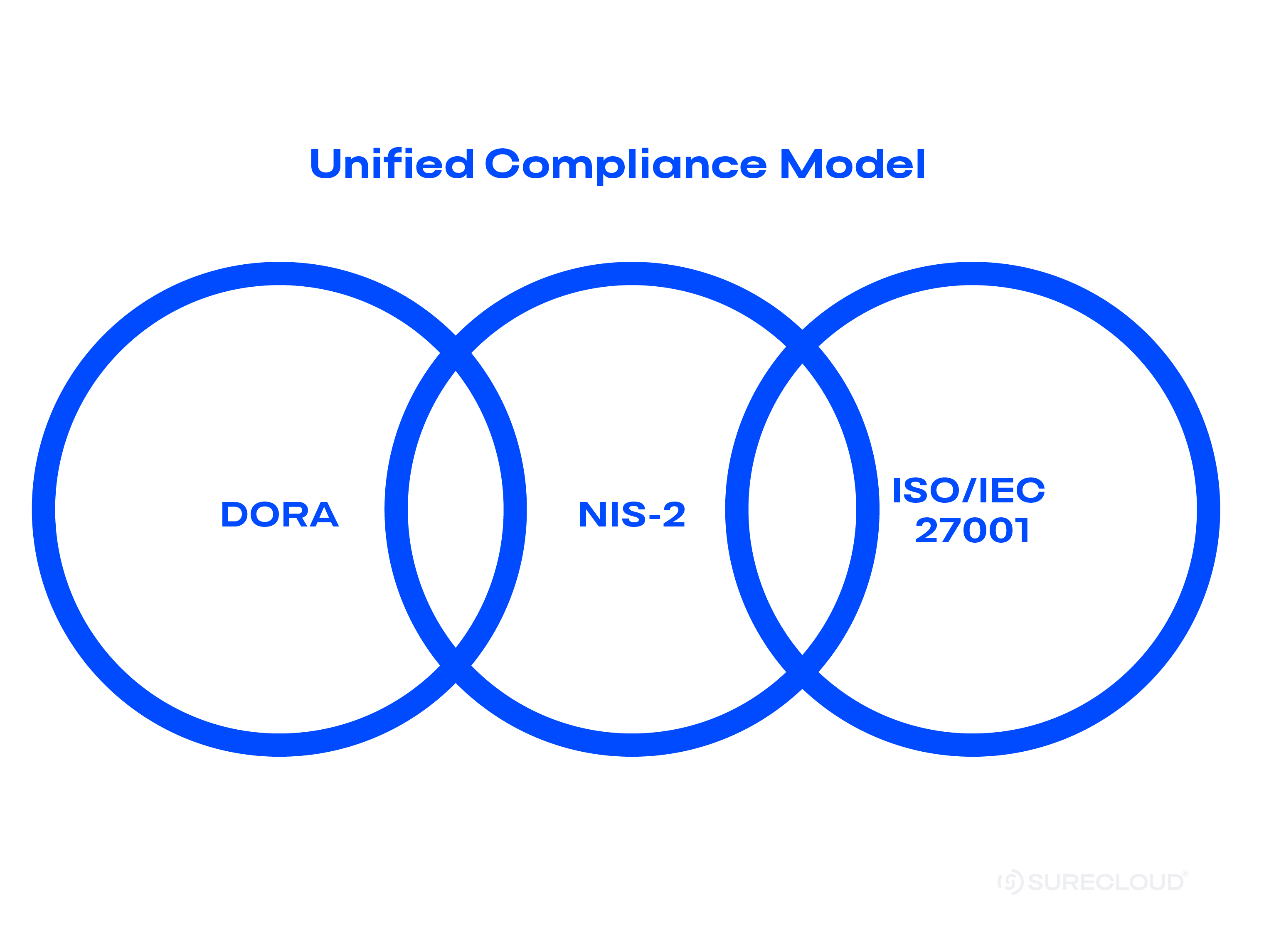
- Shared DNA, different scopes: DORA, NIS-2, and ISO/IEC 27001 all drive governance, risk management, incident response, and resilience—but differ in legal status, reporting timelines, and sector reach.
-
Map once, reuse everywhere: Build one unified control set and evidence library that maps to all three frameworks, reducing duplication and audit fatigue.
-
Align language and workflows: Normalise control names, harmonise incident timelines, and link artefacts to obligations so each framework view draws from the same data.
-
Operate one system, many lenses: With a single source of truth for controls, evidence, and reporting, teams can meet DORA, NIS-2, and ISO 27001 demands without multiplying effort.
By unifying compliance across these frameworks, organisations turn regulatory overlap into operational efficiency and make “audit-ready” their default state.
Introduction
Europe now runs on multiple cyber and resilience regimes. That’s good for outcomes, but it’s challenging when audits, evidence requests, and terminology vary by framework. Many teams duplicate work, maintain parallel trackers, and answer the same control questions in different ways.
The good news: these frameworks share a lot of DNA.
This comparison clarifies all things NIS-2, DORA and ISO 27001—and shows how to operate one control set and one evidence library that serve all three. If you need a deeper dive on DORA execution, see our unified approach in the DORA Compliance Guide.
Framework Overview
DORA (Digital Operational Resilience Act)

- Financial entities regulated in the EU
- ICT providers through contractual flow-down and, if designated, EU-level oversight of critical ICT third-party providers (CTPPs)
What it emphasizes
- Operational resilience program and ICT risk management
- Major incident reporting with prescribed clocks and fields
- Third-party oversight and subcontractor transparency
- Testing, including Threat-Led Penetration Testing (TLPT) where designated
Why duplication happens
- DORA introduces sector-specific reports, registers, and testing expectations that often sit alongside your existing security and continuity artifacts
- Teams end up maintaining DORA-specific copies of documents they already keep for ISO or general risk management unless they unify control language and evidence routing
Why it matters in this comparison
EU regulation with harmonized supervision across member states [European Commission]
NIS-2 Directive

Who it covers
Essential and important entities across sectors such as energy, transport, health, water, finance, digital infrastructure, public administration, and more.
What it emphasizes
- Cyber governance and accountability
- Risk management and incident notification to national competent authorities (NCAs)
- Supply-chain security and cooperation with NCAs.
- Incident notification timelines are defined at EU level and implemented nationally
Why duplication happens
- NIS-2 obligations are implemented via national law, so you may face different notification specifics per country in addition to DORA requirements
- Without a single register and shared control names, you can end up answering similar questions twice in different formats
Why it matters in this comparison
EU directive transposed into national law with broad cross-sector reach [ENISA]
ISO/IEC 27001 (2022 revision)

Who it covers
Any organization that wants a certifiable Information Security Management System
What it emphasizes
- Risk-based security management across people, process, and technology
- Control objectives via Annex A and continuous improvement
Why duplication happens
- ISO/IEC 27001 is the foundation for many controls, but it doesn’t set legal reporting clocks or sector-specific oversight requirements
- Without mapping, teams keep ISO evidence in one place and rebuild near-identical proof sets for DORA and NIS-2
Why it matters in this comparison
Global standard that anchors cross-framework mapping and certification [ISO]
The Common Ground: Shared Objectives
These regimes and operational resilience standards push organizations toward the same outcomes. Use the overlap to reduce duplication and reuse evidence.
- Governance and accountability: Boards and committees are active with named owners and decision rights
- Risk assessment and treatment: Ongoing assessment with treatment plans, KRIs/KPIs, and time-bound actions
- Incident response: Classification logic, escalation, communication, and post-incident reviews
- Third-party management: Tiering, required clauses, assurance artifacts, and evidence calendars
- Continuous monitoring: Control health tracking, exceptions, and retesting
- Business continuity and testing: Plans, exercises, failover tests, and lessons-learned cycles
- Documentation and traceability: Policies, procedures, registers, and logs with clear lineage to obligations
Use this table to compare obligations at a glance; cells show where a theme is explicitly required or strongly supported.
Shared objectives table
|
Theme |
DORA |
NIS-2 |
ISO/IEC 27001 |
|
Governance & accountability |
✔ |
✔ |
✔ |
|
Risk assessment & treatment |
✔ |
✔ |
✔ |
|
Incident response |
✔ with reporting clocks |
✔ with notification duties |
✔ internal IR and records |
|
Third-party management |
✔ contractual flow-downs and oversight |
✔ supply-chain security |
✔ supplier controls |
|
Continuous monitoring |
✔ control health and post-incident monitoring |
✔ ongoing risk management |
✔ ISMS performance and improvement |
|
Business continuity & testing |
✔ exercises and TLPT where designated |
✔ exercises and continuity plans |
✔ BC/DR planning and testing |
|
Documentation & traceability |
✔ templates, registers, logs |
✔ plans and proof |
✔ Statement of Applicability (SoA), policies, procedures, records |
Key Differences That Matter
Small distinctions change how you plan, resource, and evidence controls.
Use this table to scan the structural differences that drive audit and reporting expectations.
|
Dimension |
DORA |
NIS-2 |
ISO/IEC 27001 |
|
Legal status |
EU regulation |
EU directive with national transposition |
Voluntary standard |
|
Sector scope |
Financial services + ICT providers |
Broad cross-sector |
Any sector |
|
Incident reporting |
Prescribed clocks and data fields to supervisors |
Notification to NCAs with national detail |
Internal incident handling, no legal clock |
|
Oversight |
Financial supervisors with ESA coordination |
National competent authorities (NCAs) |
Certification bodies and auditors |
|
Third-party oversight |
Contract clauses, subcontractor visibility, potential EU-level oversight for CTPPs |
Supply-chain security and assurance |
Supplier controls and performance |
|
Certification |
Not applicable |
Not applicable |
Accredited certification available |
What it means in audits
- DORA: expect detailed checks on registers, incident logic, testing cadence, and supplier oversight evidence
- NIS-2: expect requests to show national notification decisioning and proof of supply-chain security measures
- ISO/IEC 27001: expect ISMS governance, risk treatment, the Statement of Applicability, and certification-grade records
Mapping Controls Across Frameworks
Map once, reuse often. The goal is reuse. Map controls once, then expose them through multiple framework views.
Use this table to see how common control themes align across regimes.
|
Control theme |
DORA |
NIS-2 |
ISO/IEC 27001 |
|
ICT risk management |
Program, owners, KRIs, governance |
Baseline cyber risk management |
ISMS risk process and Annex A |
|
Documentation |
Templates, registers, logs |
Policies, plans, records |
SoA, policies, procedures, records |
|
Incident reporting |
Clocks and fields to supervisors |
Notification to NCAs |
Internal response and records |
|
Testing & BCM |
Exercises, TLPT where designated |
Exercises, continuity plans |
BC/DR planning and testing |
|
Third-party oversight |
Tiering, flow-down clauses, subcontractor transparency |
Supply-chain security and assurance |
Supplier evaluation and controls |
|
Monitoring & improvement |
Post-incident review, corrective actions |
Ongoing risk assessment and updates |
ISMS monitoring, internal audit, corrective actions |
|
Evidence & traceability |
Register of information, live logs, audit trail |
Proof of compliance and notifications |
Evidence mapped to SoA and audits |
|
Certification & audit |
Supervisory reviews and inspections |
National oversight and audits |
Accredited certification and surveillance audits |
Traceability matters because supervisors, NCAs, and certification bodies ask for different slices of the same program. Use obligation → control → artifact → report mapping so each audience sees exactly what they need without duplicate work.
Treated this way, a DORA framework comparison becomes a control-mapping exercise instead of a parallel paperwork effort.
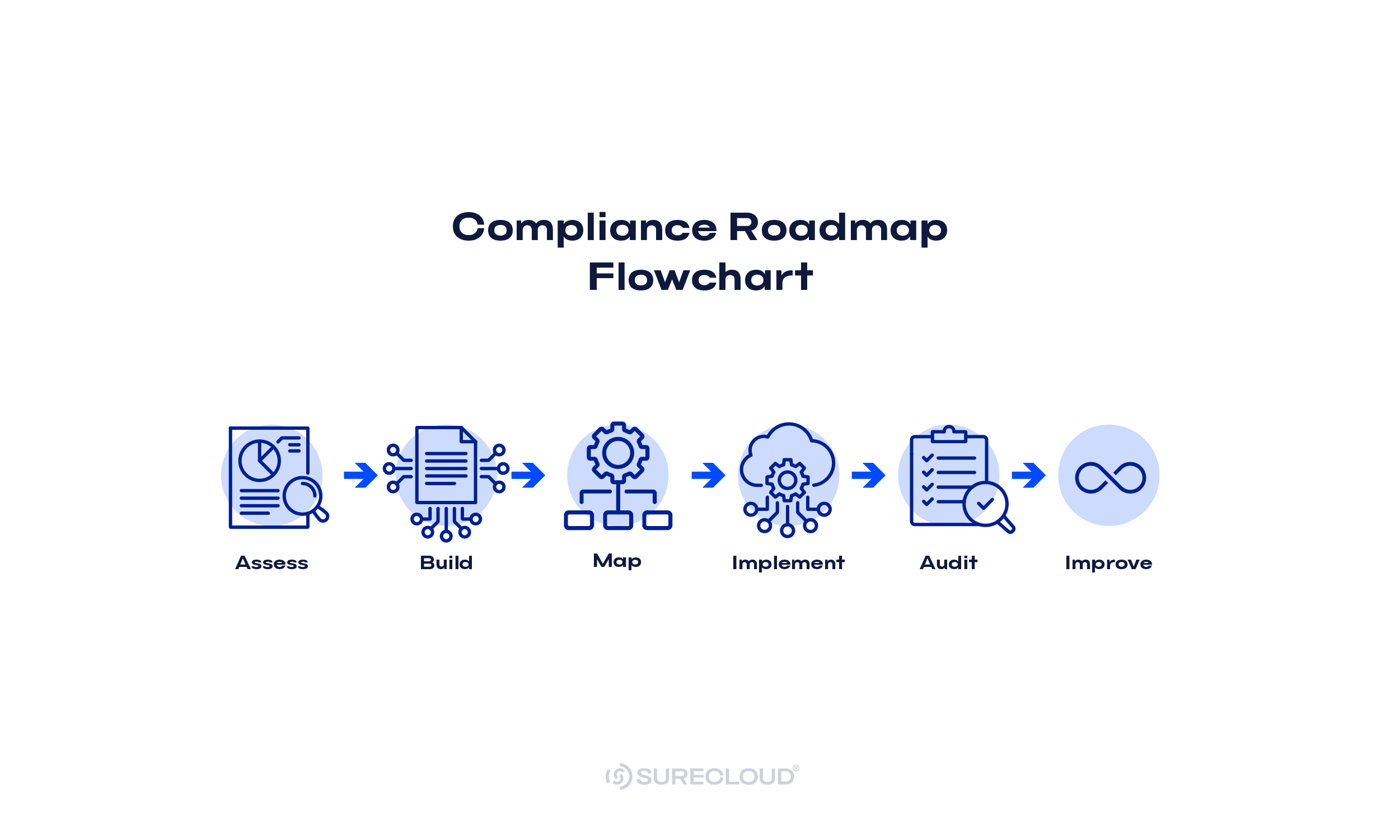
How to Combine Frameworks for Efficiency
A practical path to unify compliance and cut duplicate work.
Step 1: Map what you already have
- Start with your ISO/IEC 27001 control set and Statement of Applicability
- Map each control to DORA outcomes and NIS-2 obligations
- Capture gaps that are legal-specific, such as DORA’s incident clocks and data fields
Step 2: Consolidate one control set
- Collapse duplicates so each obligation points to a single control
- Assign owners, cadences, and evidence locations to every control
- Keep one register for services, systems, data, and suppliers
Step 3: Align language and artifacts
- Normalize control names so your controls read the same across frameworks
- Use consistent tagging from obligation to control to artifact
- Snapshot evidence before and after major changes so you can show what was true at the time
Step 4: Schedule testing and retesting
- Put continuity drills, security testing, and post-incident reviews on a calendar
- If designated for TLPT under DORA, integrate threat-led testing into your annual plan
- Track findings to closure and attach retest proof
Step 5: Calibrate incident workflows
- Mirror DORA-aligned fields and timelines where applicable
- Document NIS-2 notification logic and national contacts
- Route the same incident record to multiple reporting views to avoid duplicate data entry
Step 6: Report once, serve many
- Build a dashboard with switchable views by framework
- Export tailored packs for supervisors, NCAs, certification bodies, and leadership
- Keep a change log so recurring audits see progress without re-asking for basics
For a practical build of a unified reporting dashboard, see The 5 Pillars of DORA Explained
SureCloud’s Role in Unified Compliance
Run one control set, many frameworks with a system designed for governance and evidence.
Control library and continuous control monitoring
- Central control library with owners, cadences, and status
- Exception queues and retest tracking for continuous improvement
Automated evidence collection
- Pull artifacts on a schedule and capture versioned snapshots
- Tag evidence to obligations and control IDs for traceability
Incident and vendor workflows
- Forms that can mirror DORA incident fields and clocks
- Vendor register, tiering, flow-down clauses, subcontractor visibility, and audit rights in one place
Policy and document governance
- Lifecycle management, owner, cadence, and last-updated stamps
Reporting and audit packs
- Multi-framework dashboards and exportable evidence packs for supervisors, NCAs, certification bodies, and leadership.
Next Steps For Unified Compliance
FAQ’s
What is the difference between DORA and NIS-2?
If you’re comparing the Digital Operational Resilience Act vs NIS-2, DORA is an EU regulation for financial entities with prescriptive incident-reporting timelines and oversight of critical ICT providers, while NIS-2 is an EU directive implemented nationally across many sectors with notifications to NCAs.
Does ISO/IEC 27001 help with DORA compliance?
Yes. ISO/IEC 27001 provides a certifiable ISMS that maps well to DORA and NIS-2 themes like governance, risk management, incident response, supplier controls, and continuous improvement. You still need to meet legal specifics—such as DORA’s incident-reporting timelines and any national NIS-2 notification rules—but ISO/IEC 27001 gives you a strong control foundation and a reusable evidence model across frameworks.
“In SureCloud, we’re delighted to have a partner that shares in our values and vision.”
Read more on how Mollie achieved a data-driven approach to risk and compliance with SureCloud.
“In SureCloud, we’re delighted to have a partner that shares in our values and vision.”
Read more on how Mollie achieved a data-driven approach to risk and compliance with SureCloud.
“In SureCloud, we’re delighted to have a partner that shares in our values and vision.”
Read more on how Mollie achieved a data-driven approach to risk and compliance with SureCloud.

Reviews
Read Our G2 Reviews
4.5 out of 5
"Excellent GRC tooling and professional service"
The functionality within the platform is almost limitless. SureCloud support & project team are very professional and provide great...
Posted on
G2 - SureCloud
5 out of 5
"Great customer support"
The SureCloud team can't do enough to ensure that the software meets our organisation's requirements.
Posted on
G2 - SureCloud
4.5 out of 5
"Solid core product with friendly support team"
We use SureCloud for Risk Management and Control Compliance. The core product is strong, especially in validating data as it is...
Posted on
G2 - SureCloud
4.5 out of 5
"Excellent support team"
We've been happy with the product and the support and communication has been excellent throughout the migration and onboarding process.
Posted on
G2 - SureCloud
Product +
Frameworks +
Capabilities +
Industries +
Resources +
London Office
1 Sherwood Street, London, W1F 7BL, United Kingdom
US Headquarters
6010 W. Spring Creek Pkwy., Plano, TX 75024, United States of America
© SureCloud 2026. All rights reserved.

.png)