Resources
Expert insights for the compliance connoisseur: We cover the latest on frameworks, risks, and security trends.
All Resources
- Show All
- Blog
- Webinar
- White Paper
- Workshop
- Podcast
- Other
- Guide
- How To

- Featured
- Other
- DORA
The Complete DORA Self-Assessment
Upgrade your DORA compliance with this SureCloud readiness starter pack

- Featured
- White Paper
- GRC
The Risk Reckoning - Exclusive Industry Research report
The report captures what over 200 UK GRC leaders are really experiencing on the ground. It contrasts leadership perception with operational reality, revealing where gaps, risks, and opportunities lie across compliance, risk management, and governance.

- Featured
- Other
- GRC
Get your free RFP template for GRC software
In the process of analysing potential GRC tools? This handy request for proposal (RFP) template will help you make your final decision.
.png)
- Guide
- ISO 27001
- ISO 27002
- Third-Party Risk
The Ultimate Guide to ISO 27002: Expert Insights, Controls & Implementation
An expert guide to ISO/IEC 27002:2022. Learn the controls, updates, and best practices with real-world examples from security leaders.
- Blog
- DORA
- ISO 27001
- NIS2
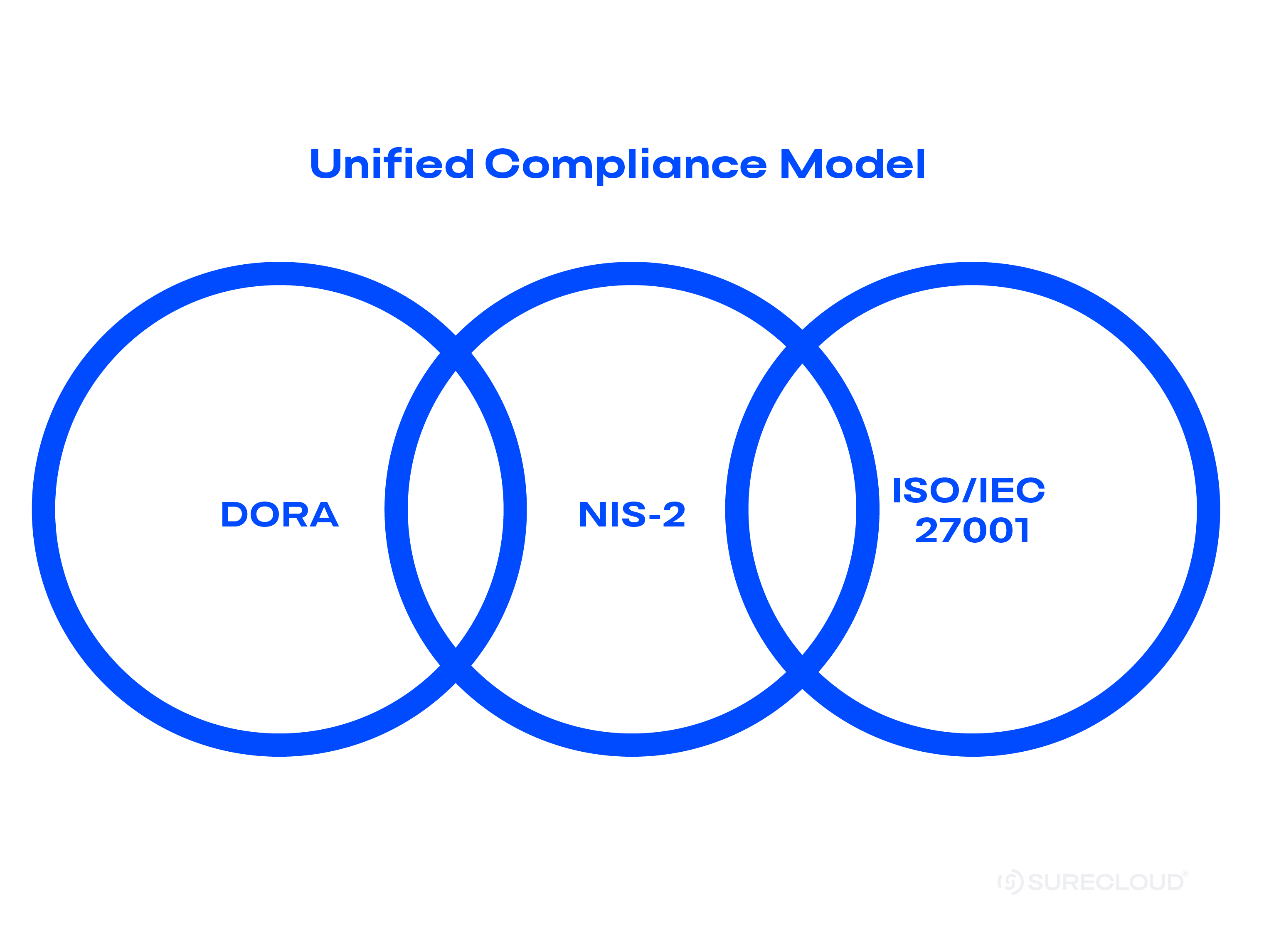
DORA vs NIS-2 vs ISO 27001: Where They Overlap & How to Combine Them
Understand how DORA, NIS-2, and ISO 27001 align. See their overlaps, gaps, and how SureCloud helps combine frameworks for simplified compliance.
.jpg)
- How To
- DORA
How to Prepare for a DORA Audit or Supervisory Review
Learn what regulators look for in DORA audits. Discover key documentation, evidence, and controls to prove operational resilience with SureCloud’s guidance.
- Guide
- DORA
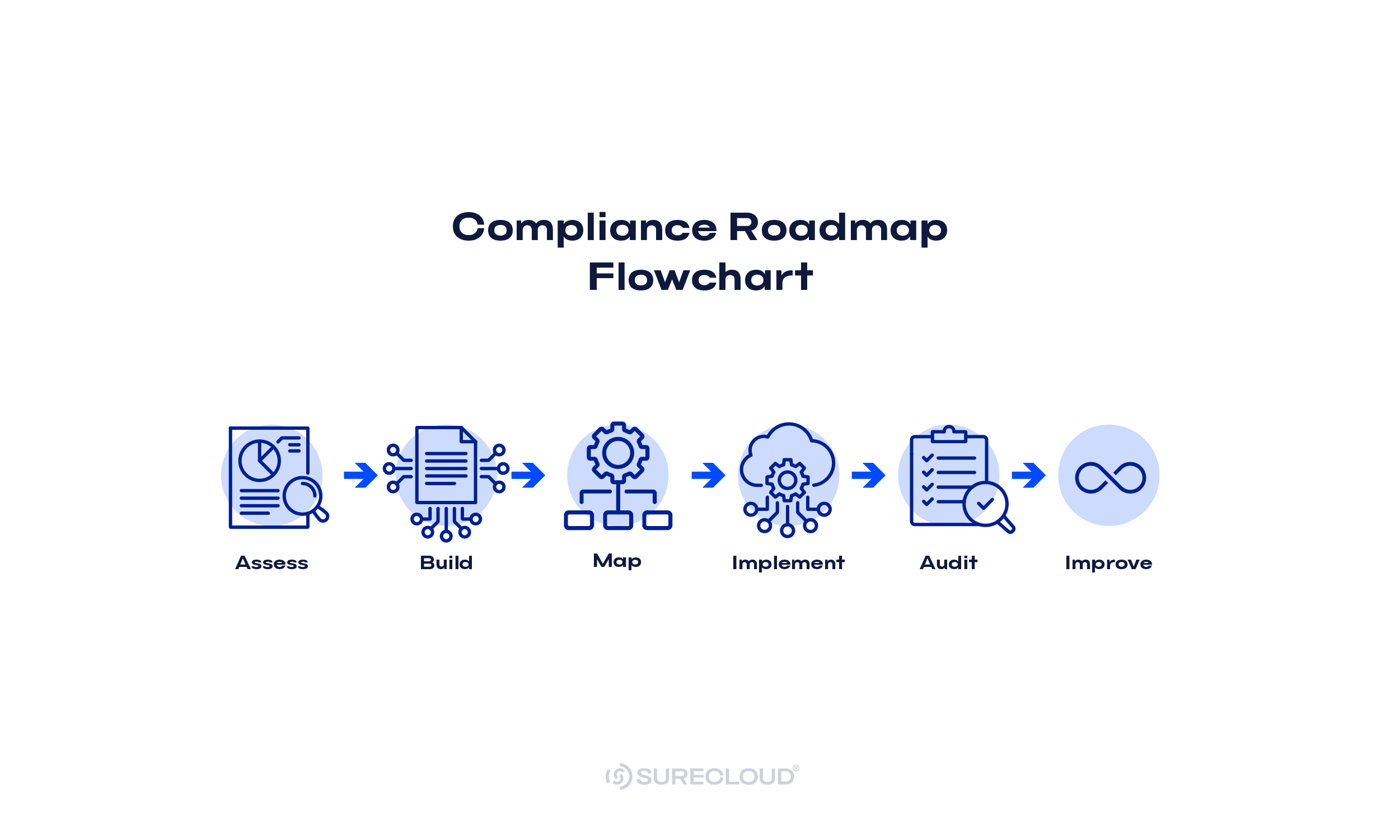
DORA Compliance Roadmap: Process, Timeline & Milestones
Explore the step-by-step DORA compliance roadmap with timelines, milestones, and how to accelerate implementation using SureCloud’s GRC platform.

- Guide
- DORA
What DORA Means for Banks, Fintechs & Insurers in 2026
Discover how DORA impacts banks, fintechs, and insurers in 2026. Learn compliance priorities, audit expectations, and how SureCloud helps.
- Blog
- DORA
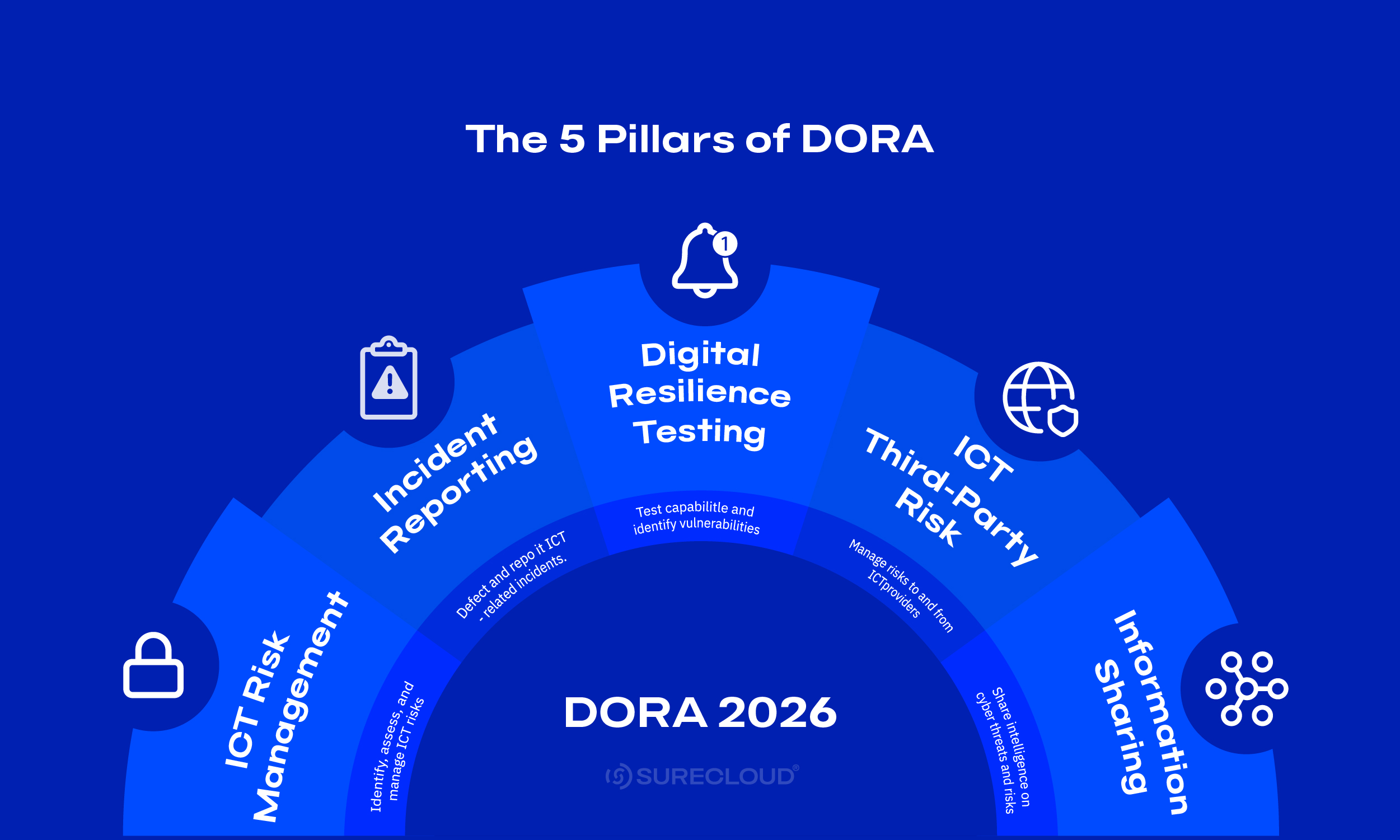
The 5 Pillars of DORA Explained – Building Digital Resilience in Financial Services
Discover the five core pillars of DORA compliance and how each strengthens operational resilience across financial services.

- Guide
- ISO 27001
- Compliance
Beginners Guide to ISO 27001
Discover what ISO 27001 means for your business, why it matters to your resilience strategy, and how to achieve certification with confidence.

Download Pricing Brochure
Transparent pricing from SureCloud
See How Our Solutions Deliver Real Results
See how our proven solutions have empowered organizations to achieve resilience, efficiency, and measurable results. Download our exclusive case study collection and explore how we deliver assurance in action.

Reviews
Read Our G2 Reviews
4.5 out of 5
"Excellent GRC tooling and professional service"
The functionality within the platform is almost limitless. SureCloud support & project team are very processional and provide great...
Posted on
G2 - SureCloud
5 out of 5
"Great customer support"
The SureCloud team can't do enough to ensure that the software meets our organisation's requirements.
Posted on
G2 - SureCloud
4.5 out of 5
"Solid core product with friendly support team"
We use SureCloud for Risk Management and Control Compliance. The core product is strong, especially in validating data as it is...
Posted on
G2 - SureCloud
4.5 out of 5
"Excellent GRC tooling and professional service"
The functionality within the platform is almost limitless. SureCloud support & project team are very processional and provide great...
Posted on
G2 - SureCloud
4.5 out of 5
"Excellent support team"
We've been happy with the product and the support and communication has been excellent throughout the migration and onboarding process.
Posted on
G2 - SureCloud
5 out of 5
"Great customer support"
The SureCloud team can't do enough to ensure that the software meets our organisation's requirements.
Posted on
G2 - SureCloud
4.5 out of 5
"Solid core product with friendly support team"
We use SureCloud for Risk Management and Control Compliance. The core product is strong, especially in validating data as it is...
Posted on
G2 - SureCloud
4.5 out of 5
"Excellent GRC tooling and professional service"
The functionality within the platform is almost limitless. SureCloud support & project team are very processional and provide great...
Posted on
G2 - SureCloud
5 out of 5
"Great customer support"
The SureCloud team can't do enough to ensure that the software meets our organisation's requirements.
Posted on
G2 - SureCloud
4.5 out of 5
"Solid core product with friendly support team"
We use SureCloud for Risk Management and Control Compliance. The core product is strong, especially in validating data as it is...
Posted on
G2 - SureCloud
4.5 out of 5
"Excellent GRC tooling and professional service"
The functionality within the platform is almost limitless. SureCloud support & project team are very processional and provide great...
Posted on
G2 - SureCloud
4.5 out of 5
"Excellent support team"
We've been happy with the product and the support and communication has been excellent throughout the migration and onboarding process.
Posted on
G2 - SureCloud
5 out of 5
"Great customer support"
The SureCloud team can't do enough to ensure that the software meets our organisation's requirements.
Posted on
G2 - SureCloud
4.5 out of 5
"Solid core product with friendly support team"
We use SureCloud for Risk Management and Control Compliance. The core product is strong, especially in validating data as it is...
Posted on
G2 - SureCloud
4.5 out of 5
"Excellent GRC tooling and professional service"
The functionality within the platform is almost limitless. SureCloud support & project team are very processional and provide great...
Posted on
G2 - SureCloud
5 out of 5
"Great customer support"
The SureCloud team can't do enough to ensure that the software meets our organisation's requirements.
Posted on
G2 - SureCloud
4.5 out of 5
"Solid core product with friendly support team"
We use SureCloud for Risk Management and Control Compliance. The core product is strong, especially in validating data as it is...
Posted on
G2 - SureCloud
4.5 out of 5
"Excellent GRC tooling and professional service"
The functionality within the platform is almost limitless. SureCloud support & project team are very processional and provide great...
Posted on
G2 - SureCloud
London Office
1 Sherwood Street, London,
W1F 7BL, United Kingdom
US Headquarters
6010 W. Spring Creek Pkwy., Plano,
TX 75024, United States of America
© SureCloud 2025. All rights reserved.

.png)










_HighPerformer_Enterprise_HighPerformer.png)








