.png?width=189&height=505&name=Vector%20(2).png)
BeyondTrust Remote Support Privilege Escalation (CVE-2019-11491)
The Tool
During an engagement last year we were asked to review the deployment of a variety of remote support and automation tools for one of our clients. One of the deployed tools was Bomgar/Beyond Trust Remote Support. It’s similar in functionality to other remote support tools like LogMeIn and GoTo Assist.
The Elevation
The tldr; is that we found a privilege escalation vulnerability that leveraged a race condition in their “Elevation Service”.
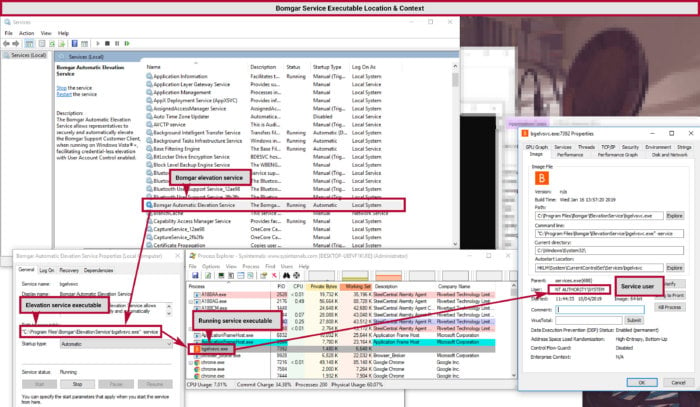
The Elevation System is an additional feature used to allow technicians to be granted temporary admin privileges on a system without the need to manage local Windows security groups. The privileges of who can use the Elevation Service is handled by the Beyond Trust Remote Support app.
Once the Elevation Service is installed, a Windows service is created named “Bomgar Automatic Elevation Service”. The service is comprised of the bgelvsvc.exe executable running under the high-privilege SYSTEM account.
When an end-user begins a support session, they download and run an executable provided by entering a code in the support portal. This executable, bomgar-scc-[randomstring].exe, is then run by the end user. Once started, the executable is deleted, and a set of new applications are created and started within the C:\ProgramData folder.
If the elevation service is not installed, this is where the workflow ends and the technician is granted access with the same permissions as the user requesting support. In this workflow any elevated requests require the technician to authenticate with their own credentials.
If the elevation service is installed, the temporary application which was placed in the C:\ProgramData folder submits a command over the named pipe BgElvSvc. The command submitted over the named pipe requests the execution of the file path C:\ProgramData\bomgar-scc-[hex value]\bomgar-scc.exe. This file is then checked by the Elevation Service and executed as SYSTEM if the checks are passed.
While the privileges set for the folder C:\ProgramData\bomgar-scc-[hex value]prevent adding any additional files bomgar-scc.exe file can be copied to any location, the named pipe command can be given the new path and the check will still pass. But this doesn’t grant any additional access.
However, bomgar-scc.exe imports three DLL library files from its current working directory. So we dropped in an msfvenom DLL payload matching the name of the files that are being automatically imported. (DLL Hijacking)
The final exploit chain was:
- Copy the
bomgar-scc.exefile fromC:\ProgramDatato the desktop - Place a our msfvenom generated
bcrypt.dllfile on the desktop - Finally, a message was submitted to the
BgElvSvcnamed pipe requesting elevation - The elevation service checks the
bomgar-scc.exefile - Checks pass and it is executed as
SYSTEMand immediately imports the custombcrypt.dll - Our Meterpreter payload is then executed as
SYSTEM
Disclosure Timeline
- 2019-04-23: Vulnerability reported to BeyondTrust
- 2019-05-16: BeyondTrust provided test patch
- 2019-05-16: SureCloud confirmed the patch fixes the vulnerability
- 2019-06-23: Fix deployed in version 19.1.3
References

About Elliott
Elliott Thompson, one of SureCloud’s Principal Security Consultants, delivers on a variety of large and unusual pen-testing engagements. Elliott engages targets throughout Europe, Asia, and the Middle East through infrastructure testing and reverse engineering to physical, social engineering and red teaming. Elliott has also appeared on the BBC as a cybersecurity expert, is a CVE identifier, CHECK Team Leader and CREST Registered Tester.
Elliott is passionate about security and involved in various article pieces for Infosec Magazine, the BBC and the UK consumer watchdog Which?. Furthermore, last year Elliott discovered and disclosed an exploit on Android tablets, which allowed attackers full access to the device including access to the webcam, speakers and microphone.

About SureCloud
SureCloud is a provider of Gartner recognised GRC software and CREST accredited Cyber Security & Risk Advisory services. Whether buying products or services your organisation would benefit from automated workflows and insight from the award-winning SureCloud platform. All of SureCloud’s service offerings are fully compatible with the GRC suite of products enabling seamless integration of information, taking your risk programmes to the next level.
.png?width=265&height=582&name=Vector%20(3).png)









.png?width=286&height=582&name=Vector%20(7).png)

 Copy link
Copy link




