Understanding and Complying with the NIS 2 Directive
EU’s updated cybersecurity law: scope, requirements & how SureCloud helps you fulfill your obligations.

Trust Badges




NIS 2 Quick Facts
What Is NIS 2?
NIS 2 is the EU’s updated cybersecurity law (Directive (EU) 2022/2555), replacing the original NIS. It expands who is in scope, sets clearer incident reporting timelines, increases management accountability, and raises supervisory powers and fines. It was introduced to address evolving cyber threats and gaps in NIS1’s scope and enforcement—so organizations can strengthen resilience and respond consistently across Member States.
- In force: January 2023
- Transposition deadline: October 17, 2024
- NIS 1 repealed: October 18, 2024
- Applies to: “Essential” and “important” entities (non-EU providers may be in scope if they serve the EU)
- Who it’s for: CISOs and Security, Risk, and Compliance leaders at essential/important entities and ICT/digital service providers operating in or with the EU
Scope of NIS 2
Essential vs Important Entities
NIS 2 applies to “essential” and “important” entities, classified by sector and size.
Common sectors in scope include:
- Energy and transport
- Banking and financial market infrastructure
- Healthcare and water services (drinking & wastewater)
- Digital infrastructure: IXPs, DNS, TLDs, data centres
- Cloud, data hosting, and managed service providers (MSPs/MSSPs)
- Postal and courier services
- Waste management, chemicals, and food
- Manufacturers of critical products
- Certain public administration bodies
Note: Cross-border operations or a high level of criticality can also bring an organisation into NIS 2 scope.
Scope Checklist
-
Confirm sector and threshold criteria.
-
Determine entity type: essential vs. important.
-
Identify the EU “main establishment” for supervision.
-
Map ICT/third-party dependencies (MSPs/MSSPs).
-
Record group structure and cross-border services.
-
Check your Member State’s transposition guidance and competent authority requirements; note UK divergence where applicable.

NIS 2 Requirements: What You Must Do
Implement governance and risk-management measures across:
- Security policies, risk assessment, secure development, and change control
- Incident handling and business continuity (backup/DR and regular testing)
- Supply-chain security and vendor oversight (including MSP/MSSP)
Vulnerability handling, disclosure, and timely patching - Access control, asset management, monitoring, and logging
- Training and awareness for staff and leadership
Deadlines for NIS 2 EU Law — Reporting Timelines
- 24 hours: early warning
- 72 hours: incident notification (with initial assessment)
-
1 month: final report (root cause, measures, severity)
Penalties Under NIS 2
- Essential entities: up to at least €10,000,000 or at least 2% of total worldwide annual turnover (whichever is higher)
- Important entities: up to at least €7,000,000 or at least 1.4% of total worldwide annual turnover (whichever is higher)
Authorities may also impose supervisory measures (e.g., audits, binding instructions, temporary managerial bans).

NIS 2 vs NIS 1
| Area | NIS 1 | NIS 2 |
| Scope | Narrower | Expanded sectors + size-cap rules |
| Reporting | General | Harmonized windows (see “Reporting Timelines”) |
| Management | Implicit | Explicit accountability |
| Supply chain | Limited guidance | Specific oversight expectations |
| Fines | Lower ceilings | Higher minimum ceilings, harmonized |
NIS 2 expands scope, strengthens governance, harmonizes reporting windows, raises supervisory powers and penalties, and elevates supply chain oversight.
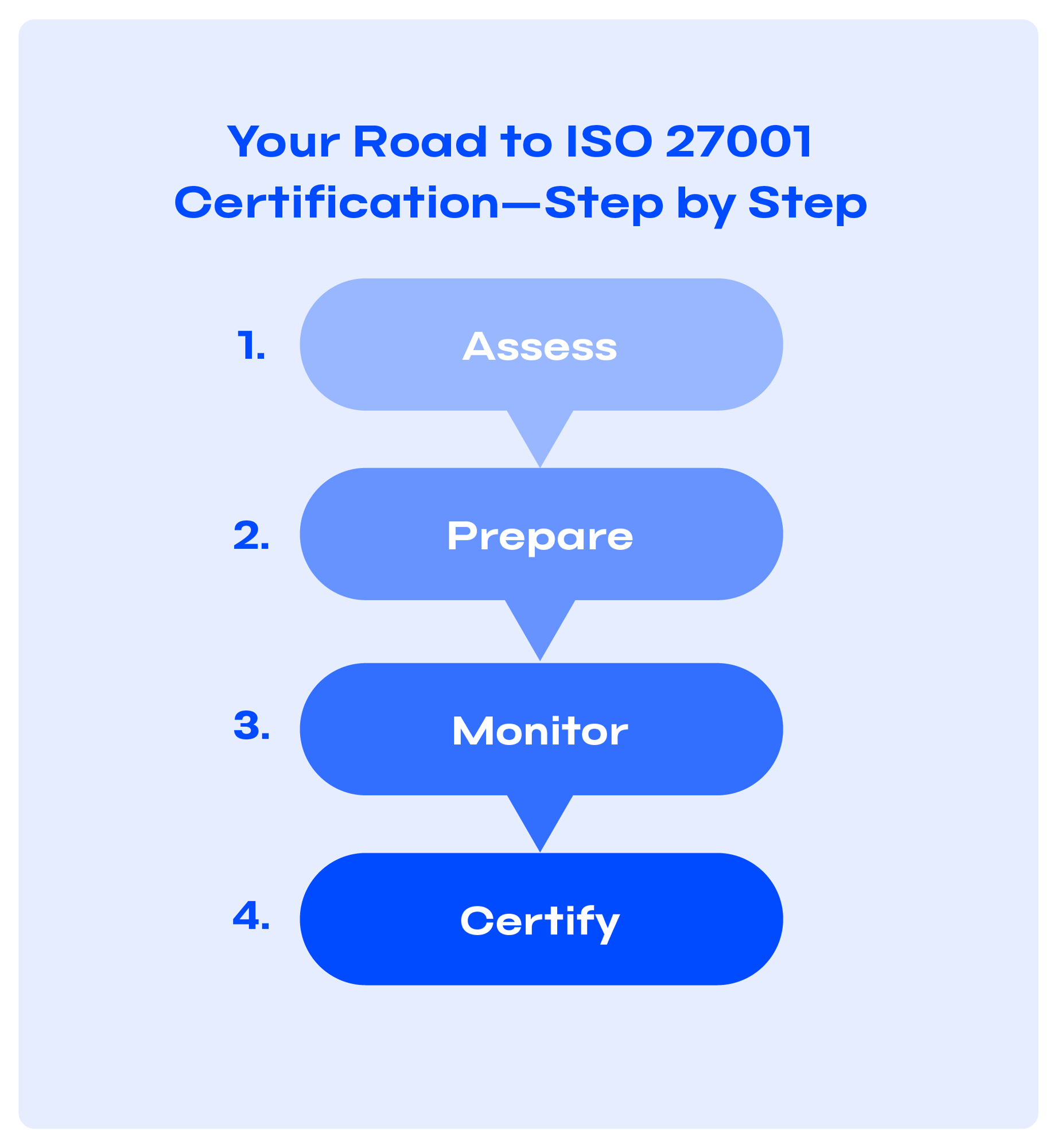
Implementation Guidance (Operational View)
Use a phased approach that ties each obligation to an owner, a control, and evidence:
- Scope & applicability: confirm entity type, sectors, and thresholds
- Gap analysis: compare current controls to NIS 2 measures
- Prioritize: address high-risk gaps first; set acceptance criteria
- Policies & processes: update, assign owners, set due dates
- Incident readiness: playbooks, contact trees, reporting templates
- Supply-chain: tier vendors/MSPs; assess, remediate, track exceptions
- Monitoring & testing: metrics, reviews, exercises, corrective actions
Reporting: dashboards for leadership and competent authorities
Evidence to
Collect
To stay audit-ready under NIS 2, organisations need clear, traceable evidence that proves controls are active and effective. This includes mapped policies and standards, approved runbooks and procedures, security tool outputs such as SIEM or vulnerability scans, and change or exception records with sign-offs. Regulators also expect proof of training and awareness, plus vendor assessment logs showing how supply-chain risks are identified and remediated. With SureCloud, all this evidence lives in one platform—linked, searchable, and ready for inspection.
- Policies/standards mapped to obligations
- Procedures/runbooks and approvals
- Tool outputs (EDR/SIEM logs, vulnerability scans)
- Change/exception tickets and sign-offs
- Training records and attestations
- Vendor assessments, issues, and remediation logs
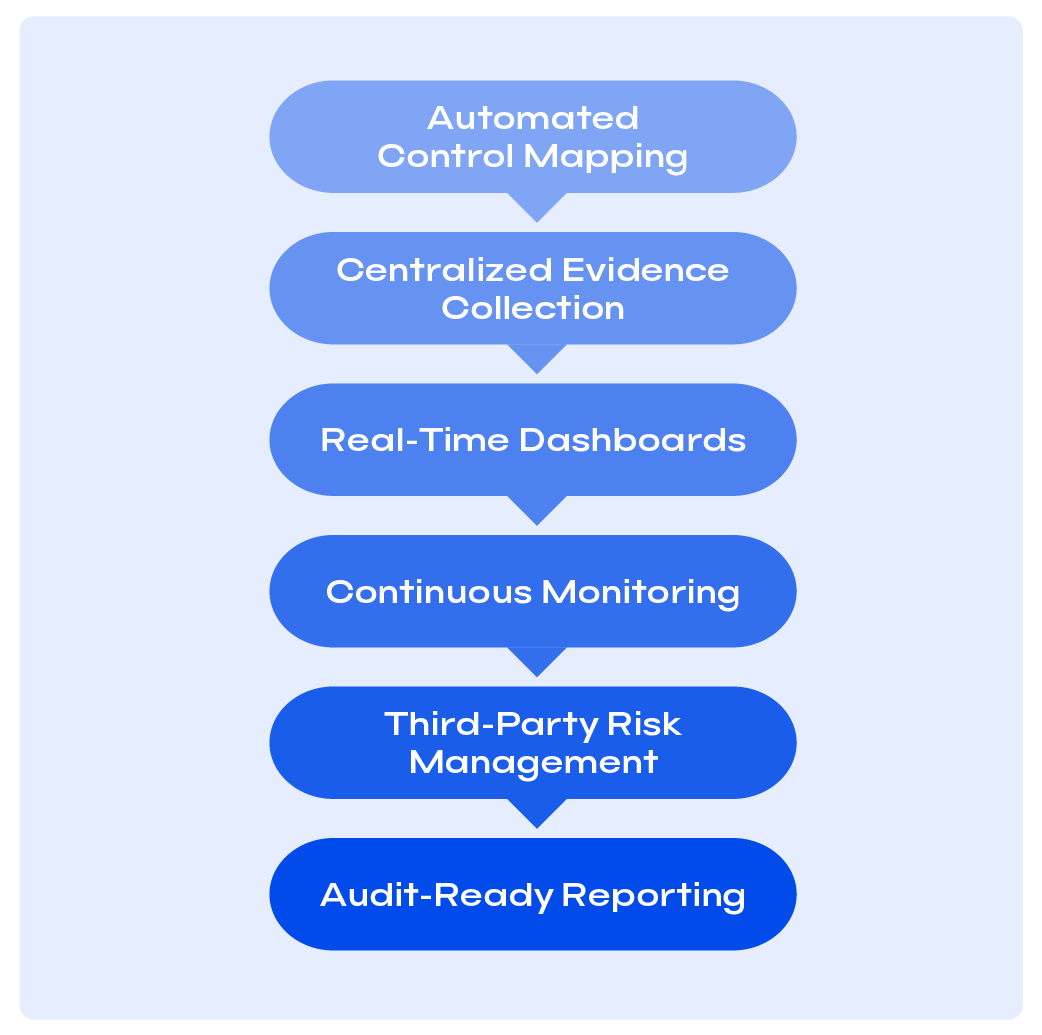
How SureCloud Makes NIS 2 Compliance Simple
Make NIS 2 obligations part of daily operations
SureCloud turns NIS 2 from a one-off project into a manageable routine. In one workspace you scope and classify (essential vs. important), map obligations, assign owners, capture evidence, oversee suppliers, and stay ready for reporting.
- Assess: Confirm essential vs. important status and sectors/thresholds (see “Scope Checklist”); map NIS 2 obligations; cross-map to ISO 27001/27002 and GDPR to reuse work.
- Implement: Assign owners and due dates; publish policies and standards; stand up technical and procedural controls; centralize evidence with approvals and version history.
- Monitor: Track control health with tasks, reviews, and tests; manage vendor risk (MSPs/MSSPs); log incidents and corrective actions against acceptance criteria.
- Report: Stay incident-reporting ready; export audit-ready packs (see “Reporting Timelines”).
Benefits of Being NIS 2 Compliant
NIS 2 compliance is more than a checkbox—it protects critical services, sharpens governance, and proves accountability. With SureCloud, you operationalize the directive and show measurable progress.
Regulatory compliance & avoiding fines
Meet obligations, hit 24 hours/72 hours/1 month timelines, and maintain audit-ready evidence to reduce enforcement and reputational risk.
Stronger cybersecurity posture and improved resilience
Apply risk-based controls, incident playbooks, and supplier oversight to lower exposure across your environment and supply chain.
Trust from customers, partners, and regulators
Share real-time dashboards and exportable reports that demonstrate control effectiveness and continuous compliance.
Clearer risk visibility, better governance
Give leaders a single view of obligations, owners, status, and gaps—driving timely decisions and accountability.
Competitive advantage
Stand out in bids and renewals with provable compliance, faster due-diligence responses, and integrated reporting across NIS-2, ISO, and GDPR.
Stand out in bids and renewals with provable compliance, faster due-diligence responses, and integrated reporting across NIS 2, ISO, and GDPR.
Ensure Your Organization Is Ready for NIS 2 Compliance
Frequently Asked Questions
When did NIS 2 come into force, and when did Member States have to implement it?
It came into force in January 2023. Member States had to transpose it by October 17, 2024; NIS 1 was repealed on October 18, 2024.
What is the difference between essential vs important entities?
Both are in scope, with differences in supervisory regime and fine ceilings. Classification depends on sector, service type, and thresholds.
What are the penalties for non-compliance?
Up to at least €10M/2% (essential) and €7M/1.4% (important), whichever is higher, plus supervisory measures as determined by competent authorities.
How long do we have to report a cybersecurity incident under NIS 2?
Early warning within 24 hours, incident notification within 72 hours, and a final report within one month.
Does NIS 2 apply to non-EU entities?
Yes, if they offer services in the EU; jurisdiction usually follows where cybersecurity decisions are made for the EU operation.
How does NIS 2 intersect with GDPR, ISO standards, and other regulations?
NIS 2 obligations for organisations overlap with ISO 27001/27002 and touch GDPR where security of processing and breach reporting intersect. Cross-mapping helps reduce duplicate effort.
.png)







_HighPerformer_Enterprise_HighPerformer.png)








