.png?width=189&height=505&name=Vector%20(2).png)
Take a look at the updates our Development team have rolled out over the Winter.
Archiving Forms and Retiring Form Templates
Default Permissions in Initiatives
Operators and Managers can do a lot more!
References expanded to fields such as dates
Colour-Only Option in Template Reports
Archiving Forms and Retiring Form Templates
The SureCloud Platform now allows users to archive Forms that are no longer needed as opposed to having to delete them. This means that the Forms once archived can still be retrieved should they be needed in the future. Similarly, Administrators can retire Form Templates.
If you are working in an Initiative where Forms have previously been archived, the “Show Archived Forms” icon will be visible on the Form tab to indicate this. This icon is shown below:-
![]()
Take a look at the updates our Development team have rolled out over the Winter.
![]()
By clicking on the icon users switch to an alternative view of the Forms tab which shows all Archived Forms in that Initiative but none of the active Forms. The “Show Archived Forms” icon is replaced by the “Hide Archived Forms” icon. This icon is shown below:-
![]()
The screenshot below gives an example corresponding to the Initiative shown above.
![]()
Forms can also be retrieved from the archives. By clicking on the “Modify Form” icon, a pop-up box appears with an “Unarchive” button. Please see below.
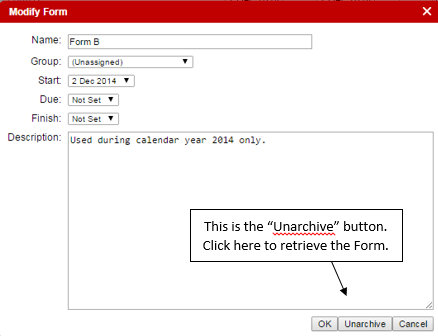
Whether or not a Form can be archived or deleted depends on the Status of the Form Template from which it was built. If the corresponding Form Template has a “Draft” status, then the Form can still be deleted, as was previously the case. If the Form Template has a “Published” or “Retired” status, then the Form can be archived.
To view or alter the Status of a Form Template, you need access to the Designer Tab in the Platform. This is available to Administrators.
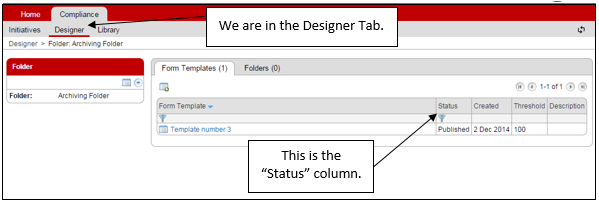
The default setting on the “Status” column is to display Form Templates which are “Not Retired”. When in the default state, “Not Retired” is written in red text at the top of the column. This can be changed by clicking on these words. Other options for the Status filter are “All”, “Draft”, “Published” and “Retired”. If one of these is chosen, you will see the filter symbol (a blue funnel) at the top of the column. This is depicted in the screenshot above.
Clicking on the “Modify Form” icon to the left of the Form Template’s name allows an Administrator to change the Status of a Form Template. See the example below.
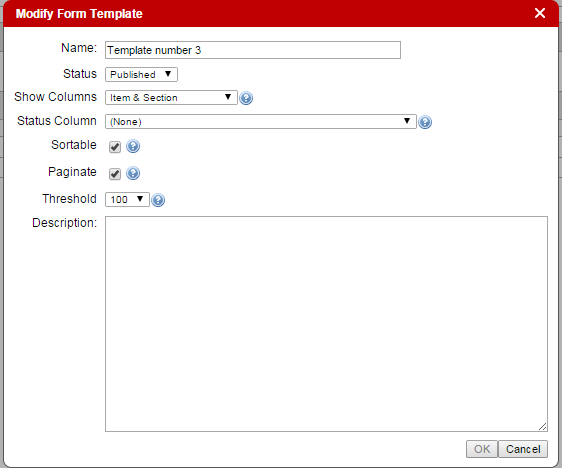
When a Form Template has been “Retired”, it is no longer provided as an option to users when they want to build a new Form in the Initiatives.
Default Permissions in Initiatives
The owner of an Initiative can set “Default Permissions” within that Initiative. If you are the owner of an Initiative, you will see a new tab called “Default Permissions”.
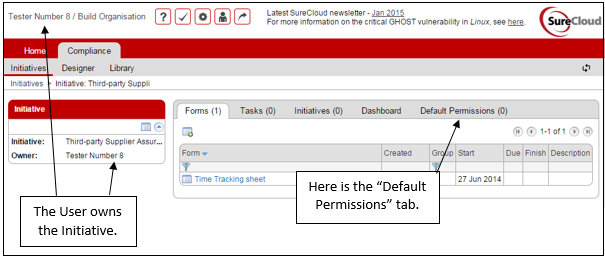
Click on the new tab. Note that the Default Permissions work within this initiative and apply to all Forms generated from selected Form Templates.
See the example below.
![]()
Click on the “Add Form Template” icon to select a new Form Template to add to the list. Once you have selected one, it will show in the list. Then you can decide on the permissions to assign to it. Click on the Form Template’s name to see a table of possible permissions to assign users to. There is an example below. Not all Form Templates will have the same Permission types to choose from.
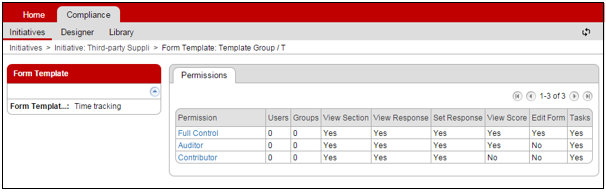
Several of the columns in this table are for information only. The fields you may adjust are the “Users” and “Groups”. Select a Permission to update by clicking on the name (in blue font). Then another table is provided as shown below.
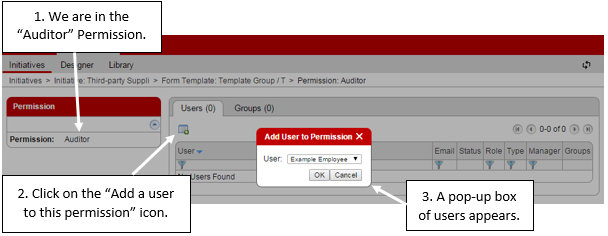
You can easily add users to the permission using the “Users” tab or you can add groups of users via the “Groups” tab.
These permissions do not apply retrospectively to Forms which have already been created in this Initiative. They will apply to new Forms as they are created. The appropriate permissions show up in the Permissions tab on the individual Forms. Default permissions in an Initiative do not apply to sub-initiatives.
Operators and Managers can do a lot more!
Operators and Managers can now create Forms. Additionally, they can do everything an Administrator can do in a Form where they have ‘full control’. For example, an Operator or Manager can set User and Group permissions on a Form they have created or have been given full control of.
Note that, an Operator or Manager can only create a Form in an Initiative that he/she already has access to. Access may be by virtue of permission on a pre-existing form or because he/she owns the Initiative or a sub-Initiative. He/she cannot add an Initiative.
Even if a contributor has been given “full control” of a Form, he/she cannot modify the Form, nor can he/she change permissions on the Form. In this case, “full control” means that the contributor can see all aspects of the Form which are visible to any other user. Contributors cannot create forms.
References expanded to fields such as dates
Administrators who use the “Designer” tab to build Form Templates or edit existing Form Templates are now able to reference a greater range of Response types in their Templates. References now work on Responses of the following types: ‘Value’, ‘Text’, ‘Option List’, ‘Formula’, ‘Date’, ‘Template’, and ‘Sequence’.
Bar Chart Colours
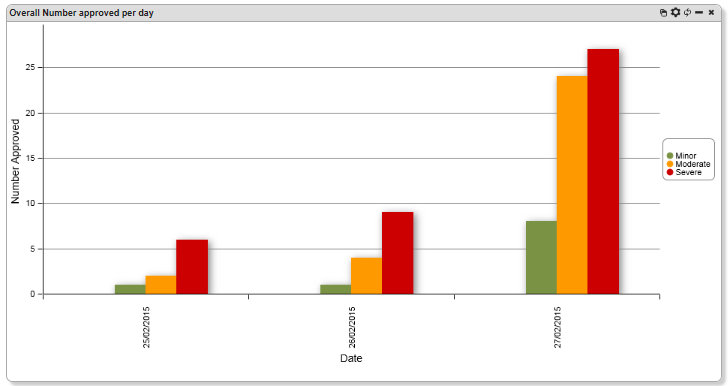
Users with Dashboards now have an extra option for their bar chart formatting. Users can select a list of colours to associate with the data in the chart. The “Colour List” option appears in the “Labels” section of the chart configuration.
The Colour List is derived from an Option List in a Form Template, so the available lists are determined by users with access to the “Designer” tab. The colouring is based on text-matching between the elements of the Option List, and the data accessed in the chart. The novelty is that the data in the chart does not have to be generated from the Option List itself, it can be the result of a Formula or similar; the Option List is just the colour guide for the bar chart.
In the following example, the data is generated by a formula.
Colour-Only Option in Template Reports
Only Administrators can set up or alter Template Reports, as they are defined in the “Designer” tab of the platform. However, Operators and Managers can see those Template Reports in their Dashboards. So this improvement is relevant to all users excluding Contributors.
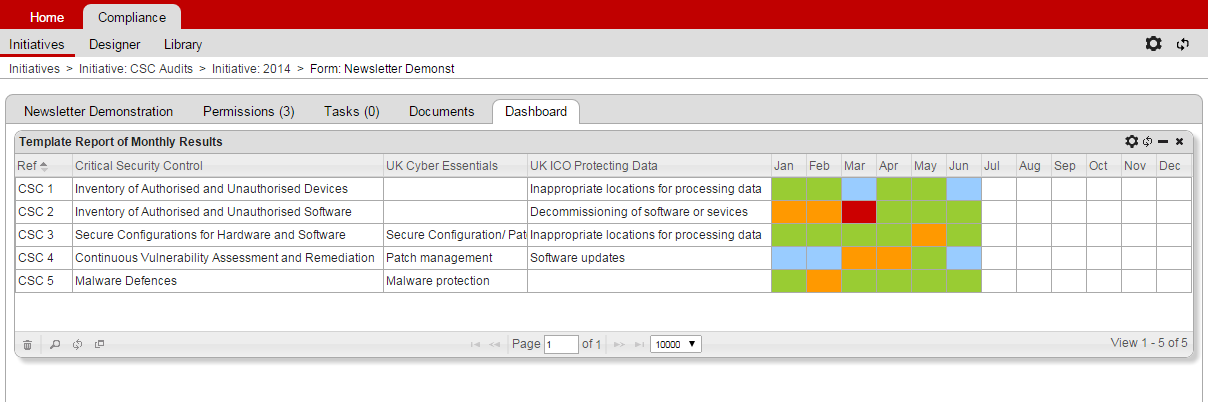
Template Reports show Form fields, not as charts, but simply as tables. If cells in the Form are coloured, that colour carries through to the Template Report. We now have the option to carry the colour only, and not the cell’s text, through to the report. See below for an example.
.png?width=265&height=582&name=Vector%20(3).png)









.png?width=286&height=582&name=Vector%20(7).png)

 Copy link
Copy link