-1.png?width=230&height=459&name=Vector%20(12)-1.png)
-1.png?width=230&height=459&name=Vector%20(12)-1.png)
Continually assess. Mitigate risk. Stay secure.
With ever-changing compliance requirements, third-party risks and a growing threat of cyberattacks, information security doesn’t stand still.
With SureCloud's Aurora platform, you don't have to take a risk with your choice of GRC software.
-1.png?width=210&height=508&name=Vector%20(13)-1.png)
Join the amazing customers who count on us to guide their GRC transformation journey
.png?width=286&height=582&name=Vector%20(7).png)
Could your organization answer
these three questions:
Are we secure?
How effective is your Information Security program and your regulatory compliance effort?
Is your program’s performance in line with your risk tolerance?
How do we know?
Can you identify, quantify and effectively manage risk?
Are you continuously assessing your risk?
How do you measure and calculate ROI?
How can we manage risk?
Do you monitor your program’s effectiveness?
How do you optimize your Information Security Management program?
Is your GRC tooling scalable?
Aurora enables complete control,visibility and optimization of information security risks
Say

to

The no-code, all-in-one GRC solution.
SureCloud’s Aurora platform helps organizations effectively manage information security risks and gain complete visibility of their operations. The highly innovative platform provides powerful insights to help your organization stay ahead of threat actors and constantly evolving compliance standards. With Aurora’s out-of-the-box automation capabilities, transform your efficiency and dramatically reduce your operating costs.
Some text goes here
Lorem ipsum dolor sit amet
Lorem ipsum dolor sit amet, consectetuer adipiscing elit, sed diam nonummy nibh euismod tincidunt.
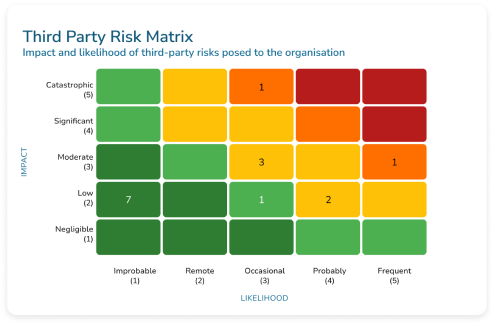
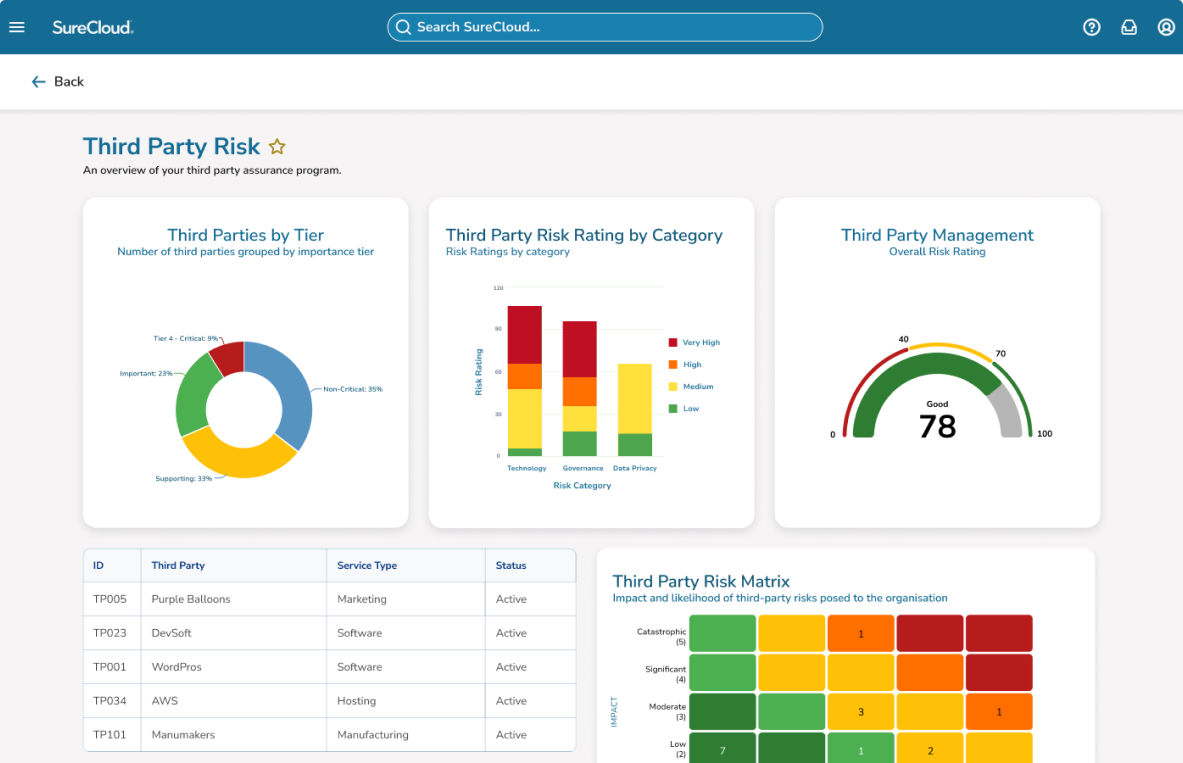
Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.

Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.

Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.

Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.

Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.

Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.

Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.

Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.

Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Arcu integer id id nam sed pharetra. Velit cursus commodo, velit sagittis etiam feugiat. Sem aenean auctor vel massa aliquam. In enim hac fermentum ac convallis semper scelerisque. Netus tincidunt lacus, ullamcorper placerat sit.

Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Arcu integer id id nam sed pharetra. Velit cursus commodo, velit sagittis etiam feugiat. Sem aenean auctor vel massa aliquam. In enim hac fermentum ac convallis semper scelerisque. Netus tincidunt lacus, ullamcorper placerat sit.
Some text goes here
Lorem ipsum dolor sit amet
Lorem ipsum dolor sit amet, consectetuer adipiscing elit, sed diam nonummy nibh euismod tincidunt.
Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.
Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.
Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.
Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.
Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.
Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.
Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.
Third-party risk
management (TPRM)
As companies expand their horizons, they increasingly rely on third-party vendors, suppliers and service providers to keep the wheels of their operations turning smoothly.
However, with great opportunity comes great risk. It’s this delicate balance between opportunity and risk that makes robust TPRM so critical.
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Arcu integer id id nam sed pharetra. Velit cursus commodo, velit sagittis etiam feugiat. Sem aenean auctor vel massa aliquam. In enim hac fermentum ac convallis semper scelerisque. Netus tincidunt lacus, ullamcorper placerat sit.
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Arcu integer id id nam sed pharetra. Velit cursus commodo, velit sagittis etiam feugiat. Sem aenean auctor vel massa aliquam. In enim hac fermentum ac convallis semper scelerisque. Netus tincidunt lacus, ullamcorper placerat sit.
Software
What’s your challenge?
No matter your information security challenge, get it covered with Aurora.

Third-party risk
management (TPRM)
Third-party relationships come with great opportunities – think reducing costs and access to specialist skills. However, third-party relationships also come with substantial risks if not managed correctly. It’s this delicate balance between managing the opportunity and risk associated with your vendors that makes robust TPRM so critical.
Fortunately, the Aurora TPRM solution is here to help you centralize and streamline your processes - and help keep you secure.
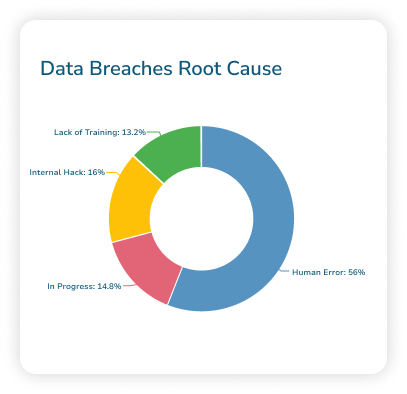
Data privacy management
By having a comprehensive approach to managing data privacy, your organization can build and maintain trust, prove compliance and demonstrate transparency.
An integrated approach to data privacy management is a must if your business is looking for a way to protect personal data in an increasingly complex and interconnected regulatory environment. Does your organization have the right technology and processes in place to protect data and build trust?
It's time to say hello to Aurora.

Compliance management
As organisations grow and scale their business operations and move into new markets, compliance requirements grow expectantly in complexity and volume.
But does your organization have the right technology and processes in place to manage your compliance obligations and report in real-time?
It's time to meet Aurora, your ultimate solution for compliance management.
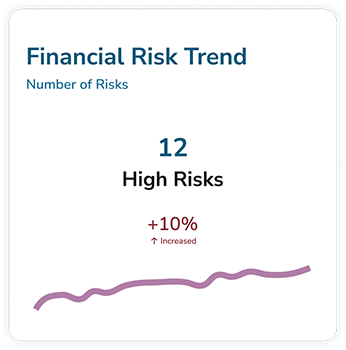
Risk Management
Your enterprise faces a range of complex, multifaceted risks. To maintain operational continuity, it’s vital that you’re equipped to first identify the risks, then manage and mitigate these risks effectively.
However, many organizations are still relying on time-consuming manual processes such as spreadsheets and Word documents. This means that they struggle to get a clear understanding of the risk landscape and remediation activities – and ultimately makes reporting a challenge.
Overcome these challenges with Aurora, built to help you monitor, manage and mitigate risks.

Internal audit management
When you’re trying to ensure your organization is working within the parameters and policies set by the board and senior management, internal auditing is vital.
But if your organization’s audits depend on a manual approach – for example, a combination of PowerPoint files, Word documents, spreadsheets and email chains, you’ve probably found that it’s anything but efficient.
It's time to change that - meet Aurora, your solution for all things internal audit management.
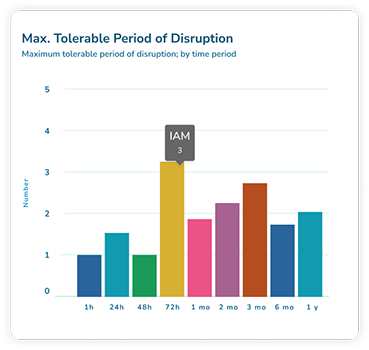
Business continuity management
In today’s world, business disruptions are an everyday occurrence. This is why having a robust business continuity plan is crucial, to get your business recovering as quickly as possible should the unexpected happen.
Having effective, reliable software takes the stress and uncertainty out of the process – which is why we designed our Aurora platform.
Find out what Aurora can do for you.
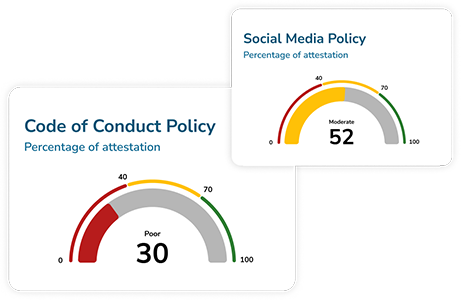
Policy management
Well-defined policies help you ensure compliance with legal requirements and industry standards and contribute to good corporate governance (as well as achieving the organizational goals, of course).
However, policy management processes can often prove a headache, with the need to manage updates, reviews and changes to (in some cases) hundreds of documents. Most organisations depend on tool such as Word and SharePoint to manage the complicated signoffs and permissions involved.
Not with Aurora - your central hub for all your policy management processes.

Incident management
Rapidly resolve unexpected disruptions
In the event of an incident, how can you take steps to resume regular service while minimizing the impact on business operations? While no one wants to face cybersecurity breaches, data leaks, or malware infections, it's critical to be prepared with an incident management plan to get back up and running swiftly and securely.
Which is exactly what Aurora is designed to help you do.
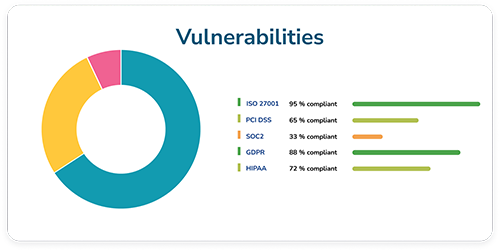
Threat & vulnerability management
For most organizations, effectively identifying, then prioritizing and managing remediation for all system vulnerabilities can feel like an almost impossible task. This is why the technology you choose should be designed to help prioritize what is most critical to your organisation to minimize the pain, cost and time associated with vulnerability management.
It's time to say hello to Aurora's vulnerability management software.
Software
What’s your challenge?
No matter your information security challenge, get it covered with Aurora.
Third-party risk
management (TPRM)
Third-party relationships come with great opportunities – think reducing costs and access to specialist skills. However, third-party relationships also come with substantial risks if not managed correctly. It’s this delicate balance between managing the opportunity and risk associated with your vendors that makes robust TPRM so critical.
Fortunately, the Aurora TPRM solution is here to help you centralize and streamline your processes - and help keep you secure.
Data privacy management
By having a comprehensive approach to managing data privacy, your organization can build and maintain trust, prove compliance and demonstrate transparency.
An integrated approach to data privacy management is a must if your business is looking for a way to protect personal data in an increasingly complex and interconnected regulatory environment. Does your organization have the right technology and processes in place to protect data and build trust?
It's time to say hello to Aurora.
Compliance management
As organisations grow and scale their business operations and move into new markets, compliance requirements grow expectantly in complexity and volume.
But does your organization have the right technology and processes in place to manage your compliance obligations and report in real-time?
It's time to meet Aurora, your ultimate solution for compliance management.
Risk Management
Your enterprise faces a range of complex, multifaceted risks. To maintain operational continuity, it’s vital that you’re equipped to first identify the risks, then manage and mitigate these risks effectively.
However, many organizations are still relying on time-consuming manual processes such as spreadsheets and Word documents. This means that they struggle to get a clear understanding of the risk landscape and remediation activities – and ultimately makes reporting a challenge.
Overcome these challenges with Aurora, built to help you monitor, manage and mitigate risks.
Internal audit management
When you’re trying to ensure your organization is working within the parameters and policies set by the board and senior management, internal auditing is vital.
But if your organization’s audits depend on a manual approach – for example, a combination of PowerPoint files, Word documents, spreadsheets and email chains, you’ve probably found that it’s anything but efficient.
It's time to change that - meet Aurora, your solution for all things internal audit management.
Business continuity management
In today’s world, business disruptions are an everyday occurrence. This is why having a robust business continuity plan is crucial, to get your business recovering as quickly as possible should the unexpected happen.
Having effective, reliable software takes the stress and uncertainty out of the process – which is why we designed our Aurora platform.
Find out what Aurora can do for you.
Policy management
Well-defined policies help you ensure compliance with legal requirements and industry standards and contribute to good corporate governance (as well as achieving the organizational goals, of course).
However, policy management processes can often prove a headache, with the need to manage updates, reviews and changes to (in some cases) hundreds of documents. Most organisations depend on tool such as Word and SharePoint to manage the complicated signoffs and permissions involved.
Not with Aurora - your central hub for all your policy management processes.
Incident management
Rapidly resolve unexpected disruptions
In the event of an incident, how can you take steps to resume regular service while minimizing the impact on business operations? While no one wants to face cybersecurity breaches, data leaks, or malware infections, it's critical to be prepared with an incident management plan to get back up and running swiftly and securely.
Which is exactly what Aurora is designed to help you do.
Threat & vulnerability management
For most organizations, effectively identifying, then prioritizing and managing remediation for all system vulnerabilities can feel like an almost impossible task. This is why the technology you choose should be designed to help prioritize what is most critical to your organisation to minimize the pain, cost and time associated with vulnerability management.
It's time to say hello to Aurora's vulnerability management software.
SureCloud: Security, elevated.
We’re a leading provider of GRC products, helping professionals like you reinvent how you manage risk. With our team of experts and innovative Aurora platform, we help organizations make better decisions to achieve their desired business outcomes. Unlike other GRC platform providers who force organizations to adapt their processes, Aurora is highly configurable and easily customized to fit your own unique operating model. – it's why our clients get immediate value from the outset and impact that lasts.
We’ve been doing great
things for a little while...
Case studies from some of our amazing customers.
.png?width=106&height=442&name=Vector%20(9).png)
Downloads
Resources
The latest articles, insights, case studies and whitepapers on all things information security.
EBook - The Ultimate Guide: The Definitive Third-Party Risk Management Maturity Journey
In our latest guide, we explore how to improve your vendor risk management program with SureCloud’s practical 7 stage model. Read more here.
Third-Party Risk
eBook - The Definitive IT Compliance Management Maturity Journey
In our latest expert guide, we explore how to improve your compliance management program with SureCloud’s practical 7 stage model. Read more.
Compliance
Template - Third-Party Tiering Assessment Template
Our helpful template allows you to gain 100% vendor coverage and prioritise your vendors effectively. Download your copy here!
Third-Party Risk
Ready to transform uncertainty into knowledge?
Whether you’re ready to take a discovery call or just want to chat through your challenges with an expert, we’d love to hear from you.